Question 291
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically destroyed. Which of the following factors is the regulation intended to address?
Question 292
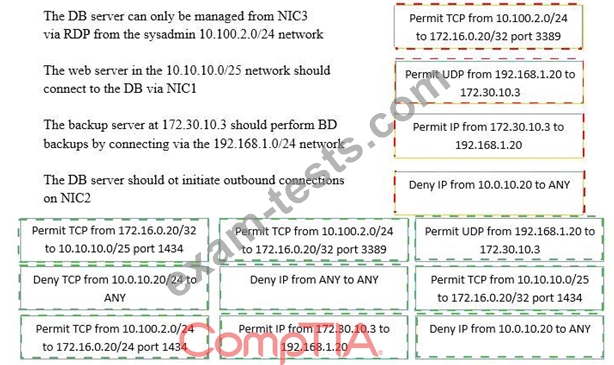
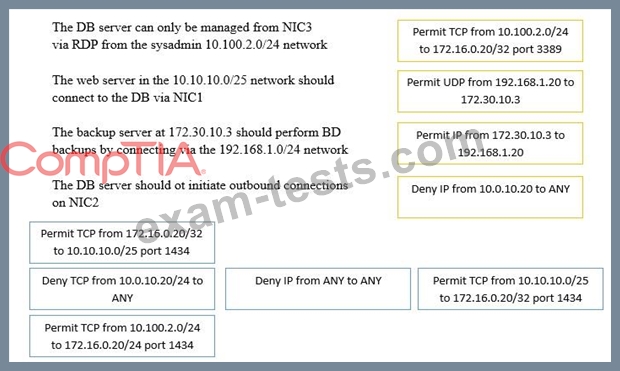
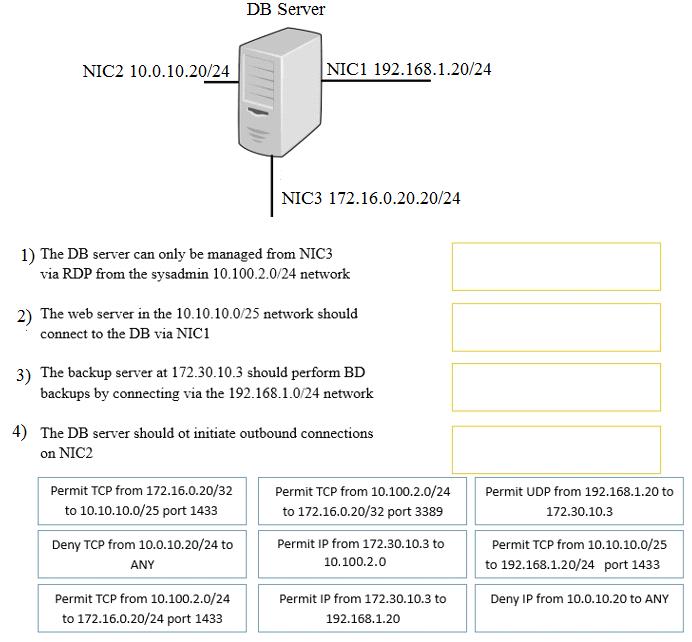
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.



Question 293
A security analyst is inspecting pseudocode of the following multithreaded application:
1. perform daily ETL of data
1.1 validate that yesterday's data model file exists
1.2 validate that today's data model file does not exist 1.2 extract yesterday's data model
1.3 transform the format
1.4 load the transformed data into today's data model file 1.5 exit
Which of the following security concerns is evident in the above pseudocode?
1. perform daily ETL of data
1.1 validate that yesterday's data model file exists
1.2 validate that today's data model file does not exist 1.2 extract yesterday's data model
1.3 transform the format
1.4 load the transformed data into today's data model file 1.5 exit
Which of the following security concerns is evident in the above pseudocode?
Question 294
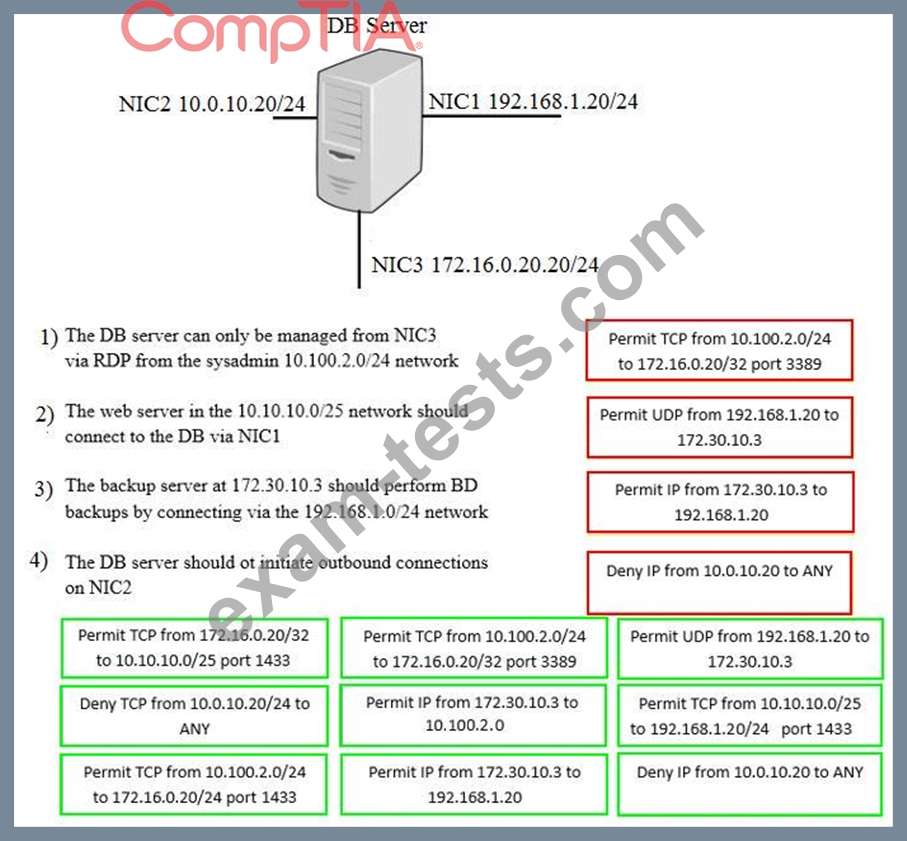
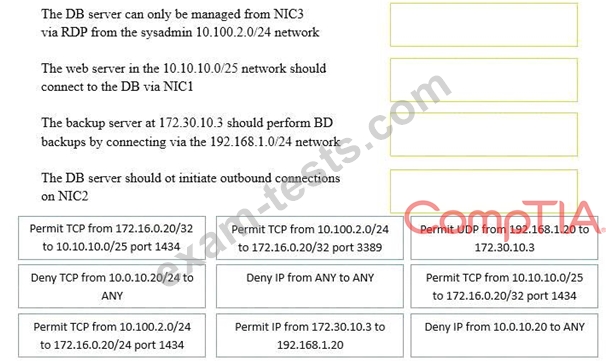
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Question 295
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live.
The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.
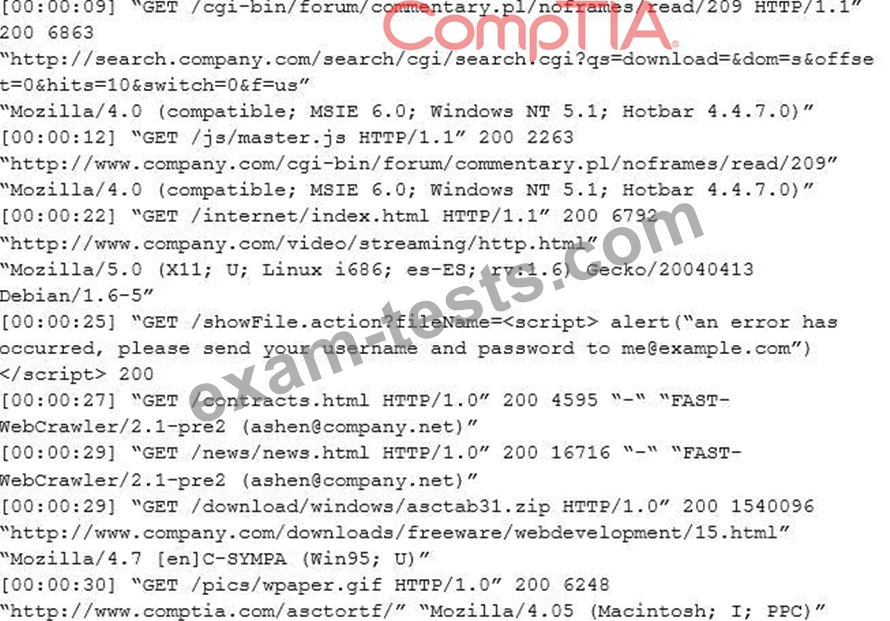
Which of the following types of attack vector did the penetration tester use?
The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.

Which of the following types of attack vector did the penetration tester use?