Question 276
An infrastructure team is at the end of a procurement process and has selected a vendor.
As part of the final negotiations, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability
2. The data will be hosted and managed outside of the company's geographical location The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant on the project, which of the following should the project's security consultant recommend as the NEXT step?
As part of the final negotiations, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability
2. The data will be hosted and managed outside of the company's geographical location The number of users accessing the system will be small, and no sensitive data will be hosted in the solution. As the security consultant on the project, which of the following should the project's security consultant recommend as the NEXT step?
Question 277
A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router:
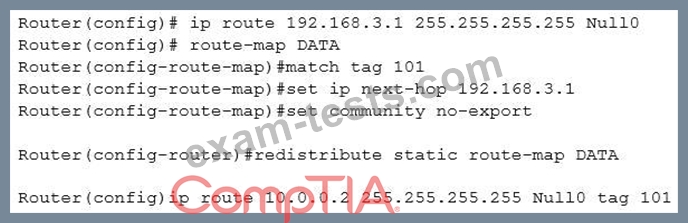
Which of the following is the engineer implementing?

Which of the following is the engineer implementing?
Question 278
An organization's network engineering team recently deployed a new software encryption solution to
ensure the confidentiality of data at rest, which was found to add 300ms of latency to data read-write
requests in storage, impacting business operations.
Which of the following alternative approaches would BEST address performance requirements while
meeting the intended security objective?
ensure the confidentiality of data at rest, which was found to add 300ms of latency to data read-write
requests in storage, impacting business operations.
Which of the following alternative approaches would BEST address performance requirements while
meeting the intended security objective?
Question 279
ABC Corporation has introduced token-based authentication to system administrators due to the risk of password compromise. The tokens have a set of HMAC counter-based codes and are valid until they are used.
Which of the following types of authentication mechanisms does this statement describe?
Which of the following types of authentication mechanisms does this statement describe?
Question 280
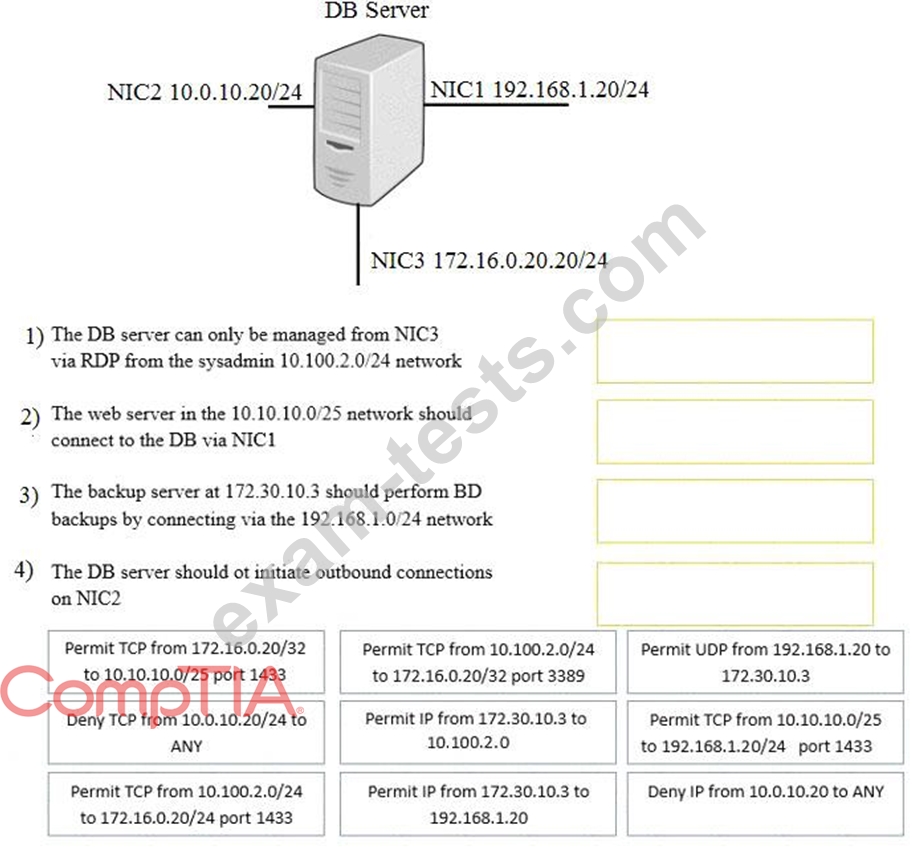
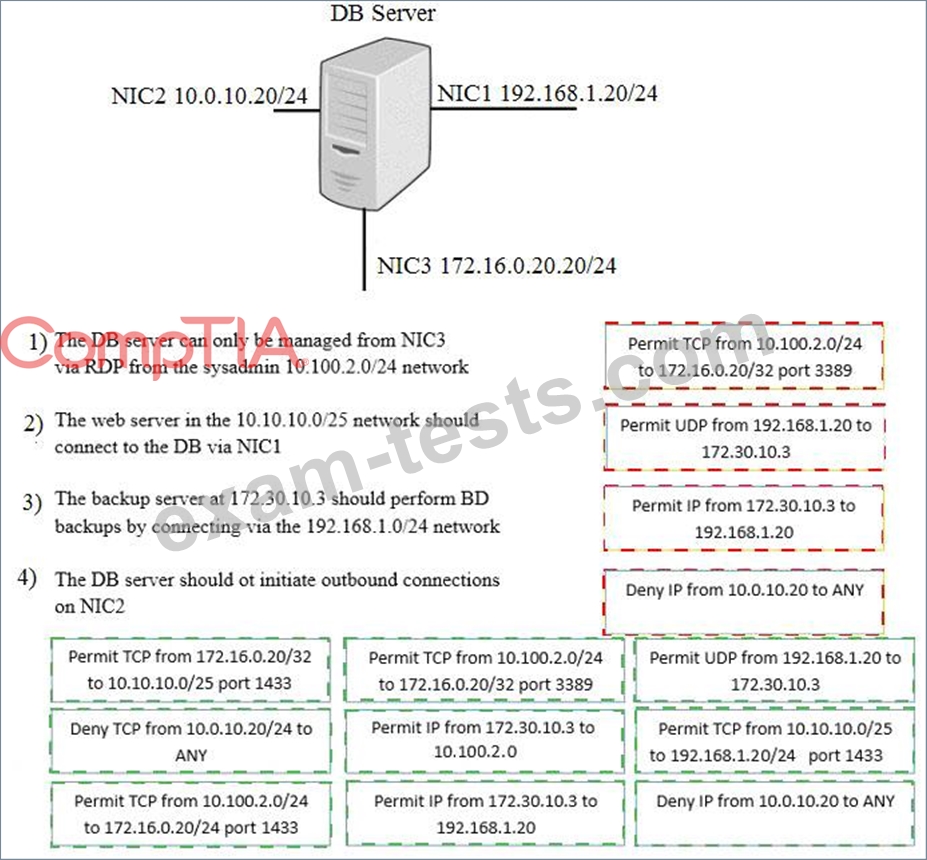
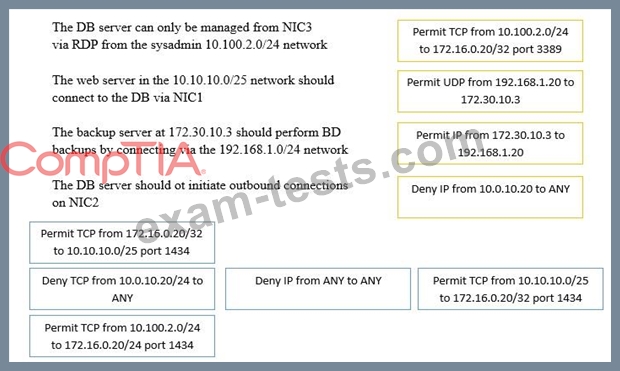
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.