Question 331
A risk manager has decided to use likelihood and consequence to determine the risk of an event occurring to a company asset. Which of the following is a limitation of this approach to risk management?
Question 332
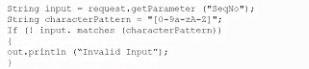
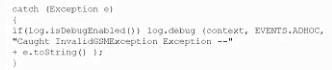
A system engineer is reviewing output from a web application vulnerability scan. The engineer has determined data is entering the application from an untrusted source and is being used to construct a query dynamically.
Which of the following code snippets would BEST protect the application against an SQL injection attack?
A)
B)
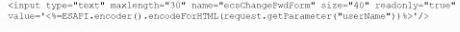
C)
D)
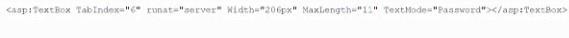
Which of the following code snippets would BEST protect the application against an SQL injection attack?
A)

B)
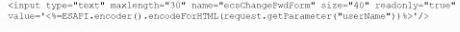
C)

D)
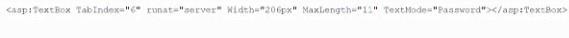
Question 333
A government contractor was the victim of a malicious attack that resulted in the theft of sensitive information. An analyst's subsequent investigation of sensitive systems led to the following discoveries:
* There was no indication of the data owner's or user's accounts being compromised.
* No database activity outside of previous baselines was discovered.
* All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
* It was likely not an insider threat, as all employees passed polygraph tests.
Given this scenario, which of the following is the MOST likely attack that occurred?
* There was no indication of the data owner's or user's accounts being compromised.
* No database activity outside of previous baselines was discovered.
* All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
* It was likely not an insider threat, as all employees passed polygraph tests.
Given this scenario, which of the following is the MOST likely attack that occurred?
Question 334
A company provides on-demand cloud computing resources for a sensitive project. The company implements a fully virtualized datacenter and terminal server access with two-factor authentication for customer access to the administrative website. The security administrator at the company has uncovered a breach in data confidentiality. Sensitive data from customer A was found on a hidden directory within the VM of company B.
Company B is not in the same industry as company A and the two are not competitors. Which of the following has MOST likely occurred?
Company B is not in the same industry as company A and the two are not competitors. Which of the following has MOST likely occurred?
Question 335
Which of the following is an external pressure that causes companies to hire security assessors and penetration testers?

