Question 326
The Chief Executive Officer (CEO) of a company that allows telecommuting has challenged the Chief Security Officer's (CSO) request to harden the corporate network's perimeter. The CEO argues that the company cannot protect its employees at home, so the risk at work is no different. Which of the following BEST explains why this company should proceed with protecting its corporate network boundary?
Question 327
An administrator is tasked with securing several website domains on a web server. The administrator elects to secure www.example.com, mail.example.org, archive.example.com, and www.example.org with the same certificate. Which of the following would allow the administrator to secure those domains with a single issued certificate?
Question 328
Confidential information related to Application A.
Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:
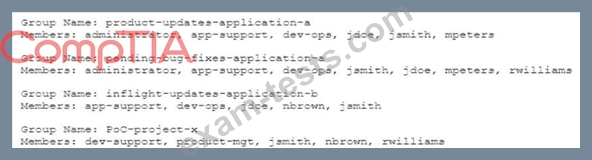
Which of the following actions should the IR team take FIRST?
Application B and Project X appears to have been leaked to a competitor. After consulting with the legal team, the IR team is advised to take immediate action to preserve evidence for possible litigation and criminal charges.
While reviewing the rights and group ownership of the data involved in the breach, the IR team inspects the following distribution group access lists:

Which of the following actions should the IR team take FIRST?
Question 329
Given the following:
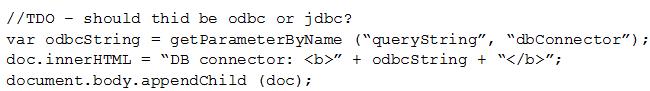
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 330
A security analyst is validating the MAC policy on a set of Android devices. The policy was written to ensure non-critical applications are unable to access certain resources. When reviewing dmesg, the analyst notes many entries such as:
Despite the deny message, this action was still permit following is the MOST likely fix for this issue?
Despite the deny message, this action was still permit following is the MOST likely fix for this issue?

