Question 346
An organization is selecting a SaaS provider to replace its legacy, in house Customer Resource Management (CRM) application. Which of the following ensures the organization mitigates the risk of managing separate user credentials?
Question 347
An organization is improving its web services to enable better customer engagement and self-service. The organization has a native mobile application and a rewards portal provided by a third party. The business wants to provide customers with the ability to log in once and have SSO between each of the applications. The integrity of the identity is important so it can be propagated through to back-end systems to maintain a consistent audit trail. Which of the following authentication and authorization types BEST meet the requirements? (Choose two.)
Question 348
An organization is reviewing endpoint security solutions. In evaluating products, the organization has the following requirements:
1. Support server, laptop, and desktop infrastructure
2. Due to limited security resources, implement active protection capabilities
3. Provide users with the ability to self-service classify information and apply policies
4. Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Select two.)
1. Support server, laptop, and desktop infrastructure
2. Due to limited security resources, implement active protection capabilities
3. Provide users with the ability to self-service classify information and apply policies
4. Protect data-at-rest and data-in-use
Which of the following endpoint capabilities would BEST meet the above requirements? (Select two.)
Question 349
An administrator wants to ensure hard drives cannot be removed from hosts and men installed into and read by unauthorized hosts Which of the following techniques would BEST support this?
Question 350
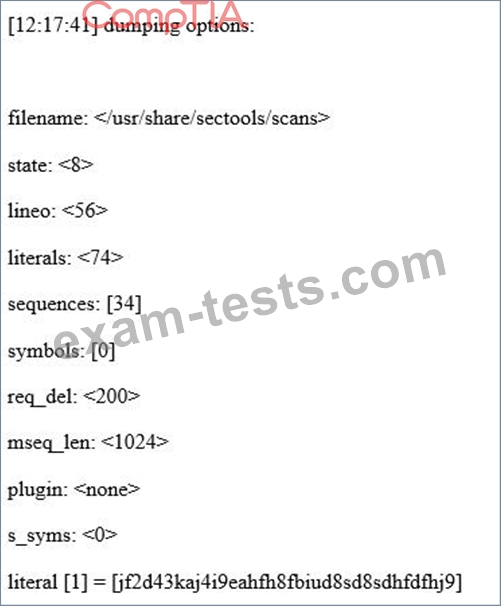
Given the following output from a security tool in Kali: