Question 486
A database administrator is required to adhere to and implement privacy principles when executing daily tasks. A manager directs the administrator to reduce the number of unique instances of PII stored within an organization's systems to the greatest extent possible. Which of the following principles is being demonstrated?
Question 487
An organization has established the following controls matrix:
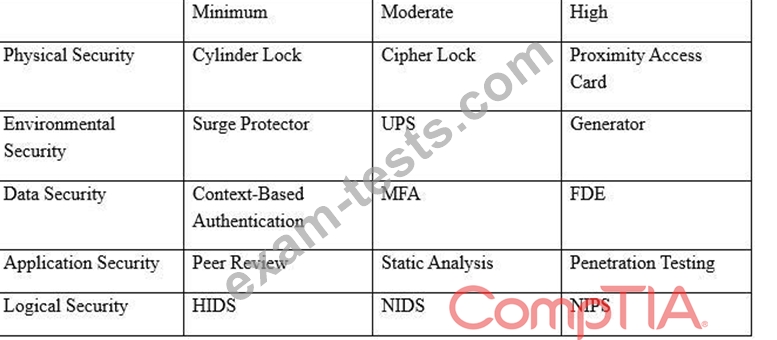
The following control sets have been defined by the organization and are applied in aggregatefashion:
* Systems containing PII are protected with the minimum control set.
* Systems containing medical data are protected at the moderate level.
* Systems containing cardholder data are protected at the high level.
The organization is preparing to deploya system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?

The following control sets have been defined by the organization and are applied in aggregatefashion:
* Systems containing PII are protected with the minimum control set.
* Systems containing medical data are protected at the moderate level.
* Systems containing cardholder data are protected at the high level.
The organization is preparing to deploya system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
Question 488
A security engineer reviews the table below:
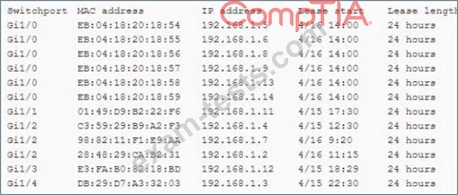
The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?

The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?
Question 489
A well-known retailer has experienced a massive credit card breach. The retailer had gone through an audit and had been presented with a potential problem on their network.
Vendors were authenticating directly to the retailer's AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept.
The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that because the vendors were required to have site to site VPN's no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
Vendors were authenticating directly to the retailer's AD servers, and an improper firewall rule allowed pivoting from the AD server to the DMZ where credit card servers were kept.
The firewall rule was needed for an internal application that was developed, which presents risk. The retailer determined that because the vendors were required to have site to site VPN's no other security action was taken.
To prove to the retailer the monetary value of this risk, which of the following type of calculations is needed?
Question 490
A company has deployed MFA Some employees, however, report they ate not gelling a notification on their mobile device Other employees report they downloaded a common authenticates application but when they tap the code in the application it just copies the code to memory instead of confirming the authentication attempt Which of the following are the MOST likely s for these scenarios? (Select TWO)

