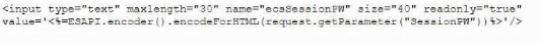Question 491
Ann, a systems engineer, is working to identify an unknown node on the corporate network. To begin her investigative work, she runs the following nmap command string:
user@hostname:~$ sudo nmap -O 192.168.1.54
Based on the output, nmap is unable to identify the OS running on the node, but the following ports are open on the device:
TCP/22
TCP/111
TCP/512-514
TCP/2049
TCP/32778
Based on this information, which of the following operating systems is MOST likely running on the unknown node?
user@hostname:~$ sudo nmap -O 192.168.1.54
Based on the output, nmap is unable to identify the OS running on the node, but the following ports are open on the device:
TCP/22
TCP/111
TCP/512-514
TCP/2049
TCP/32778
Based on this information, which of the following operating systems is MOST likely running on the unknown node?
Question 492
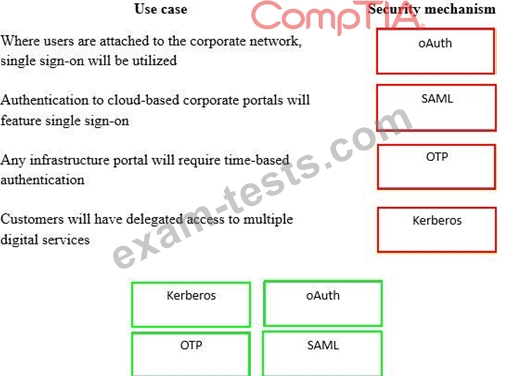
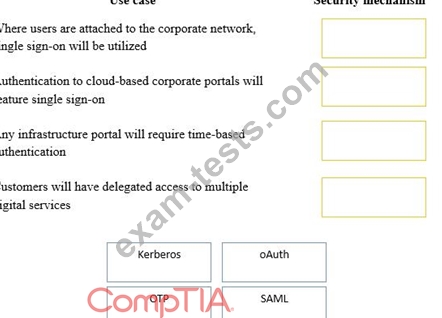
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.

Question 493
A company has implemented data retention policies and storage quotas in response to their legal department's requests and the SAN administrator's recommendation.
The retention policy states all email data older than 90 days should be eliminated.
As there are no technical controls in place, users have been instructed to stick to a storage quota of 500Mb of network storage and 200Mb of email storage.
After being presented with an e-discovery request from an opposing legal council, the security administrator discovers that the user in the suit has 1Tb of files and 300Mb of email spanning over two years.
Which of the following should the security administrator provide to opposing council?
The retention policy states all email data older than 90 days should be eliminated.
As there are no technical controls in place, users have been instructed to stick to a storage quota of 500Mb of network storage and 200Mb of email storage.
After being presented with an e-discovery request from an opposing legal council, the security administrator discovers that the user in the suit has 1Tb of files and 300Mb of email spanning over two years.
Which of the following should the security administrator provide to opposing council?
Question 494
A company is in the process of outsourcing its customer relationship management system to a cloud provider. It will host the entire organization's customer database. The database will be accessed by both the company's users and its customers. The procurement department has asked what security activities must be performed for the deal to proceed. Which of the following are the MOST appropriate security activities to be performed as part of due diligence? (Select TWO).
Question 495
A developer needs to provide feedback on a peer's work during the SDLC. While reviewing the code changes, the developers session ID tokens for a web application will be transmitted over an unsecure connection. Which of the following code snippets should the developer recommend implement to correct the vulnerability?
A)
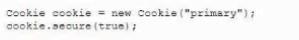
B)
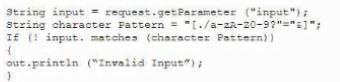
C)
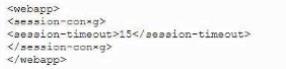
D)
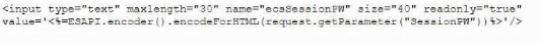
A)

B)

C)
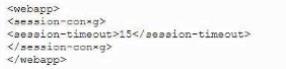
D)