Question 291
Over the last 90 days, many storage services has been exposed in the cloud services environments, and the security team does not have the ability to see is creating these instance. Shadow IT is creating data services and instances faster than the small security team can keep up with them. The Chief information security Officer (CIASO) has asked the security officer (CISO) has asked the security lead architect to architect to recommend solutions to this problem.
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
Question 292
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages:
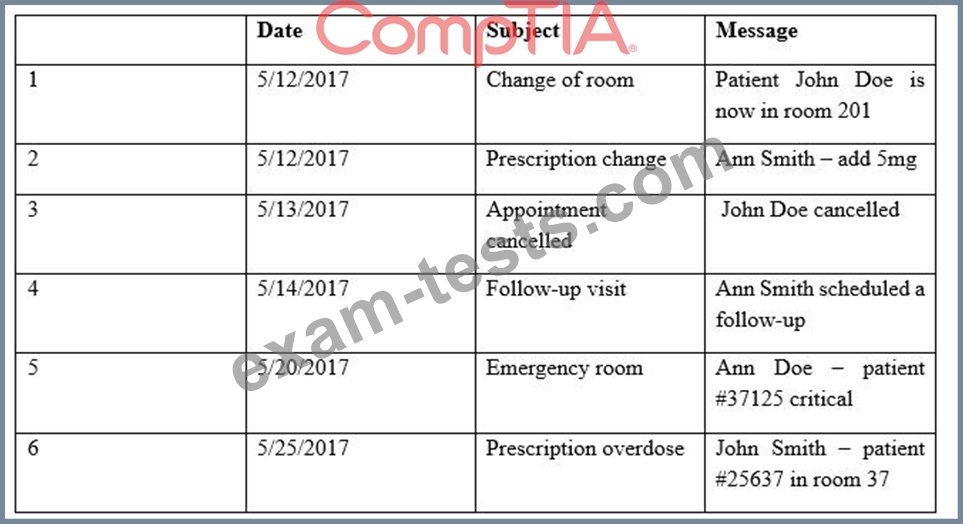
Which of the following represents the BEST solution for preventing future fines?

Which of the following represents the BEST solution for preventing future fines?
Question 293
A managed service provider is designing a log aggregation service for customers who no longer want tomanage an internal SIEM infrastructure. The provider expects that customers will send all types of logs to them, and that log files could contain very sensitive entries. Customers have indicated they want on-premises and cloud-based infrastructure logs tobe stored in this new service. An engineer, who is designing the new service, is deciding how to segment customers. Which of the following is the BEST statement for the engineer to take into consideration?
Question 294
An organization is currently working with a client to migrate data between a legacy ERP system and a
cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is
performing data deduplication and sanitization of client data to ensure compliance with regulatory
requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
cloud-based ERP tool using a global PaaS provider. As part of the engagement, the organization is
performing data deduplication and sanitization of client data to ensure compliance with regulatory
requirements. Which of the following is the MOST likely reason for the need to sanitize the client data?
Question 295
Following a major security modem that resulted in a significant loss of revenue and extended loss of server availability, a new Chief Information Security Officer (CISO) conducts a root cause analysis. Which of the following additional steps should the CISO take to mitigate the chance of a recurrence?

