Question 311
A creative services firm has a limited security budget and staff. Due to its business model, the company sends and receives a high volume of files every day through the preferred method defined by its customers. These include email, secure file transfers, and various cloud service providers. Which of the following would BEST reduce the risk of malware infection while meeting the company's resource requirements and maintaining its current workflow?
Question 312
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created.
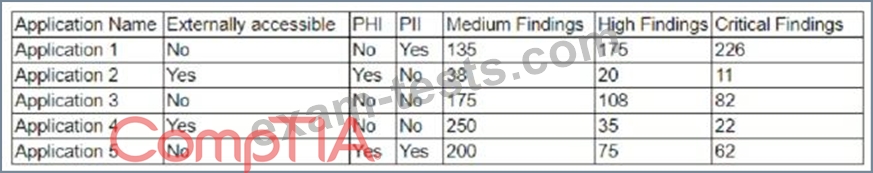
The findings are then categorized according to the following chart:
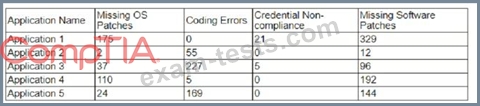
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)

The findings are then categorized according to the following chart:

Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)
Question 313
Two competing companies experienced similar attacks on their networks from various threat actors. To improve response times, the companies wish to share some threat intelligence about the sources and methods of attack. Which of the following business documents would be BEST to document this engagement?
Question 314
A security engineer is assessing the controls that are in place to secure the corporate-Internet-facing DNS server. The engineer notices that security ACLs exist but are not being used properly. The DNS server should respond to any source but only provide information about domains it has authority over. Additionally, the DNS administrator have identified some problematic IP addresses that should not be able to make DNS requests.
Given the ACLs below:

Which of the following should the security administrator configure to meet the DNS security needs?
Given the ACLs below:

Which of the following should the security administrator configure to meet the DNS security needs?
Question 315
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?

