Question 351
A technician is validating compliance with organizational policies. The user and machine accounts in the AD are not set to expire, which is non-compliant. Which of the following network tools would provide this type of information?
Question 352
A company that has been breached multiple times is looking to protect cardholder data. The previous undetected attacks all mimicked normal administrative-type behavior. The company must deploy a host solution to meet the following requirements:
* Detect administrative actions
* Block unwanted MD5 hashes
* Provide alerts
* Stop exfiltration of cardholder data
Which of the following solutions would BEST meet these requirements? (Choose two.)
* Detect administrative actions
* Block unwanted MD5 hashes
* Provide alerts
* Stop exfiltration of cardholder data
Which of the following solutions would BEST meet these requirements? (Choose two.)
Question 353
Which of the following activities is commonly deemed "OUT OF SCOPE" when undertaking a penetration test?
Question 354
A Chief Information Security Officer (CISO) has created a survey that will be distributed to managers of mission-critical functions across the organization The survey requires the managers to determine how long their respective units can operate in the event of an extended IT outage before the organization suffers monetary losses from the outage To which of the following is the survey question related? (Select TWO)
Question 355
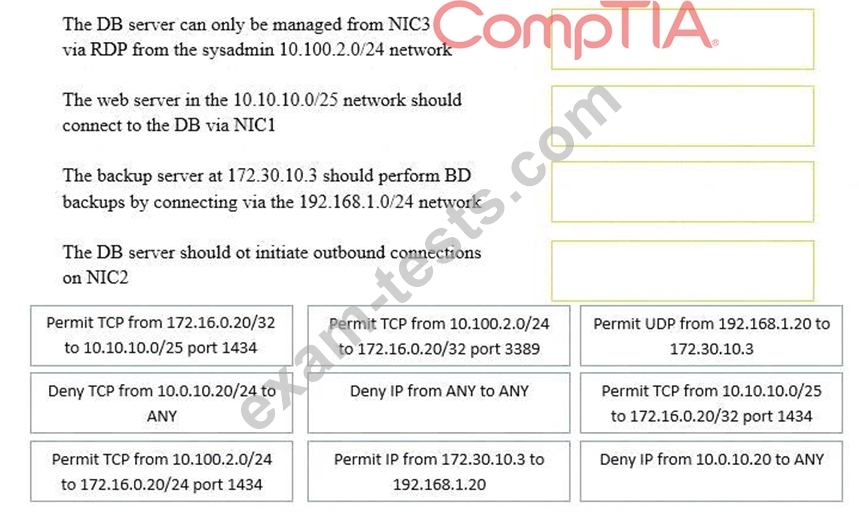
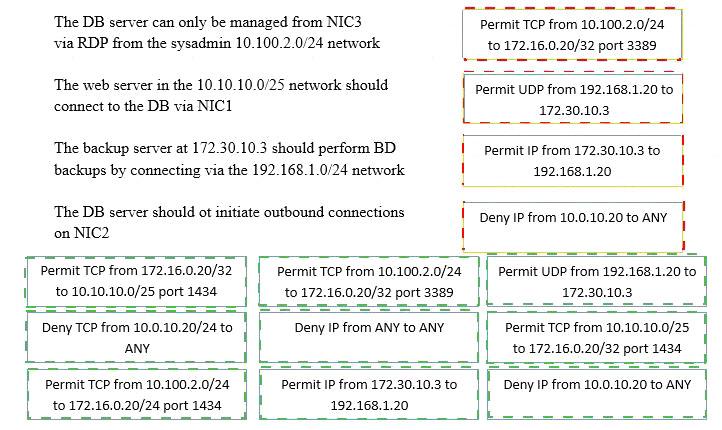
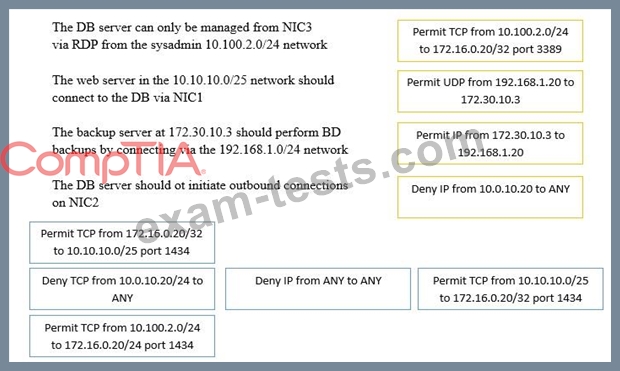
A security administrator must configure the database server shown below the comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.