Question 336
A security analyst is reviewing the following pseudo-output snippet after running the command less
/tmp/file,tmp.
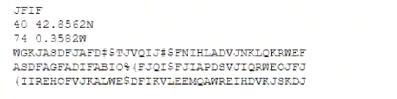
The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
/tmp/file,tmp.

The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
Question 337
A security engineer reviews the table below:
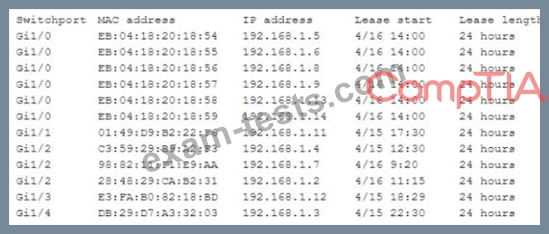
The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?

The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?
Question 338
Which of the following may indicate a configuration item has reached end-of-life?
Question 339
A hospital is deploying new imaging softwares that requires a web server for access to image for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following.
* The imaging server IP is 192.168.101.24
* The domain controller IP is 192.168.100.1
* The client machine IP is 192.168.200.37
Which of the following should be used to confirm this is the only open post on the web server?
* The imaging server IP is 192.168.101.24
* The domain controller IP is 192.168.100.1
* The client machine IP is 192.168.200.37
Which of the following should be used to confirm this is the only open post on the web server?
Question 340
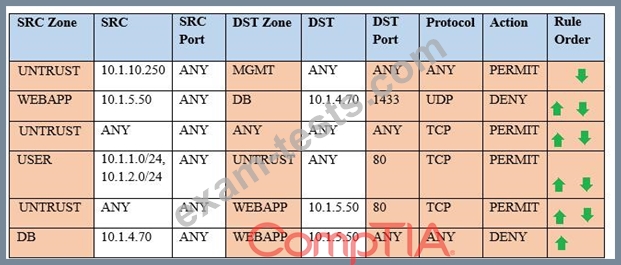
Compliance with company policy requires a quarterly review of firewall rules.
You are asked to conduct a review on the internal firewall sitting between several internal networks.
The intent of this firewall is to make traffic more secure.
Given the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation requirements, click Save. When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.

