Question 381
A company is in the process of implementing a new front end user interface for its customers, the goal is to provide them with more self-service functionality. The application has been written by developers over the last six months and the project is currently in the test phase.
Which of the following security activities should be implemented as part of the SDL in order to provide the MOST security coverage over the solution? (Select TWO).
Which of the following security activities should be implemented as part of the SDL in order to provide the MOST security coverage over the solution? (Select TWO).
Question 382
An organization enables BYOD but wants to allow users to access the corporate email, calendar, and contacts from their devices. The data associated with the user's accounts is sensitive, and therefore, the organization wants to comply with the following requirements:
Active full-device encryption
Enabled remote-device wipe
Blocking unsigned applications
Containerization of email, calendar, and contacts
Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
Active full-device encryption
Enabled remote-device wipe
Blocking unsigned applications
Containerization of email, calendar, and contacts
Which of the following technical controls would BEST protect the data from attack or loss and meet the above requirements?
Question 383
A security administrator wants to implement controls to harden company-owned mobile devices.
Company policy specifies the following requirements:
- Mandatory access control must be enforced by the OS.
- Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Select three).
Company policy specifies the following requirements:
- Mandatory access control must be enforced by the OS.
- Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Select three).
Question 384
Given the following:
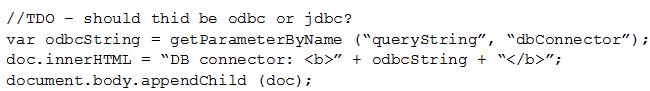
Which of the following vulnerabilities is present in the above code snippet?

Which of the following vulnerabilities is present in the above code snippet?
Question 385
Given the following code snippet:
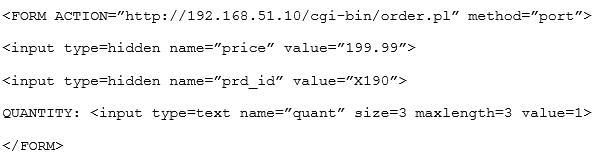
Of which of the following is this snippet an example?

Of which of the following is this snippet an example?

