Question 376
With which of the following departments should an engineer for a consulting firm coordinate when
determining the control and reporting requirements for storage of sensitive, proprietary customer
information?
determining the control and reporting requirements for storage of sensitive, proprietary customer
information?
Question 377
An organization's network security administrator has been using an SSH connection to manage switches and routers for several years. After attempting to connect to a router, an alert appears on the terminal emulation software, warning that the SSH key has changed.
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.)
After confirming the administrator is using the typical workstation and the router has not been replaced, which of the following are the MOST likely explanations for the warning message? (Choose two.)
Question 378
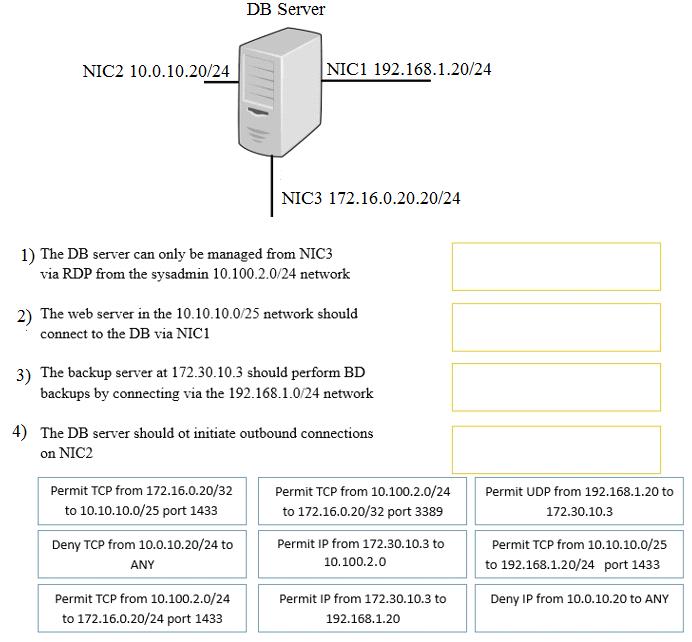
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.

Question 379
An analyst execute a vulnerability scan against an internet-facing DNS server and receives the following report:

Which of the following tools should the analyst use FIRST to validate the most critical vulnerability?

Which of the following tools should the analyst use FIRST to validate the most critical vulnerability?
Question 380
A security administrator has been asked to select a cryptographic algorithm to meet the criteria of a new application. The application utilizes streaming video that can be viewed both on computers and mobile devices. The application designers have asked that the algorithm support the transport encryption with the lowest possible performance overhead. Which of the following recommendations would BEST meet the needs of the application designers? (Select TWO).


