Question 21
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
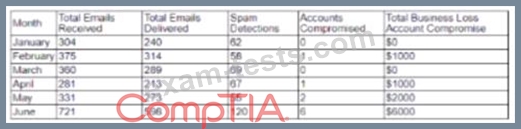

Which of the following meets the budget needs of the business?


Which of the following meets the budget needs of the business?
Question 22
A customer reports being unable to connect to a website at www.test.com to consume services. The customer notices the web application has the following published cipher suite:

Which of the following is the MOST likely cause of the customer's inability to connect?

Which of the following is the MOST likely cause of the customer's inability to connect?
Question 23
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company's Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
Which of the following will MOST likely secure the data on the lost device?
Question 24
An organization's hunt team thinks a persistent threats exists and already has a foothold in the enterprise network.
Which of the following techniques would be BEST for the hunt team to use to entice the adversary to uncover malicious activity?
Which of the following techniques would be BEST for the hunt team to use to entice the adversary to uncover malicious activity?
Question 25
A security analyst observes the following while looking through network traffic in a company's cloud log:

Which of the following steps should the security analyst take FIRST?

Which of the following steps should the security analyst take FIRST?
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

