Question 36
SIMULATION
You are a security analyst tasked with interpreting an Nmap scan output from company's privileged network.
The company's hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
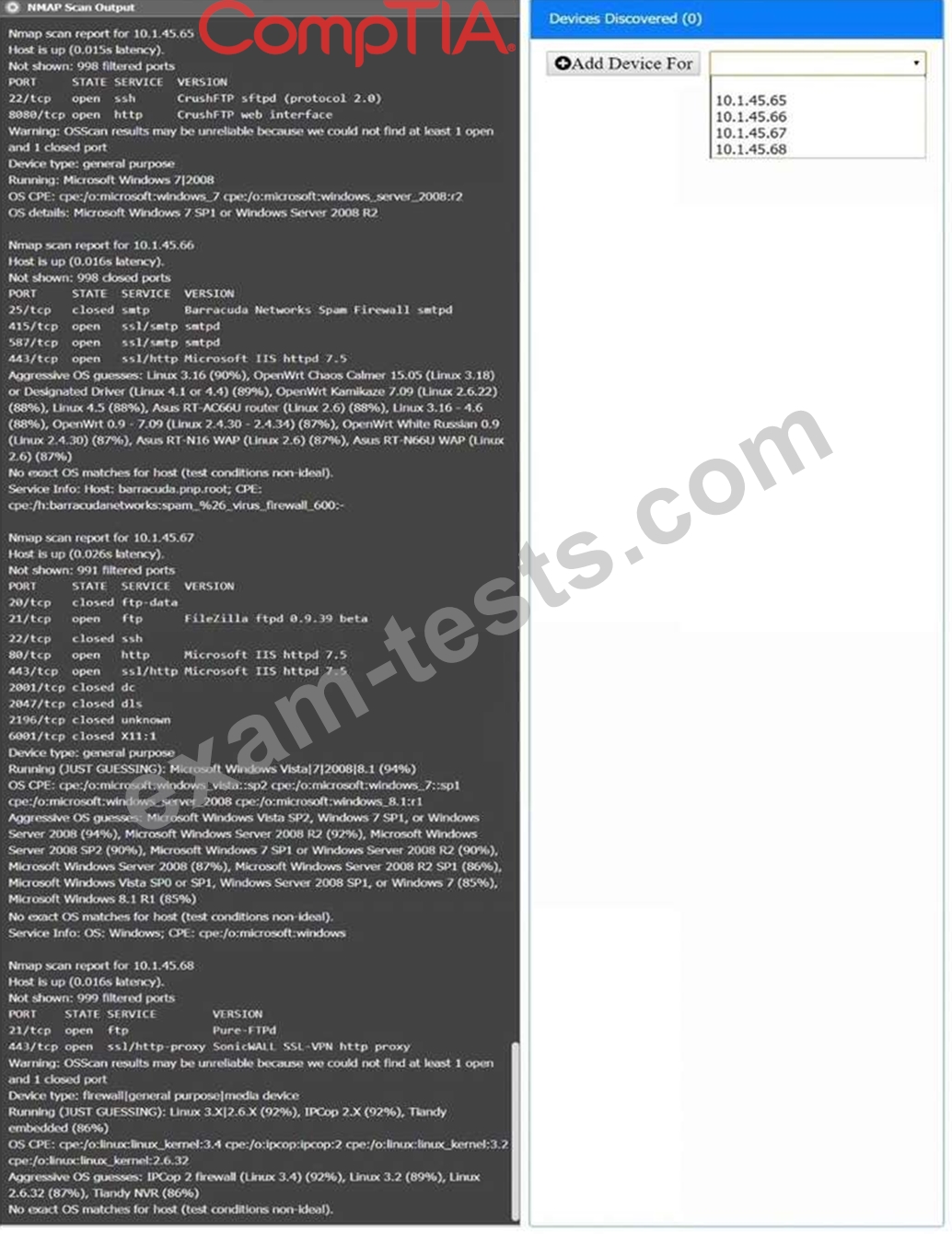
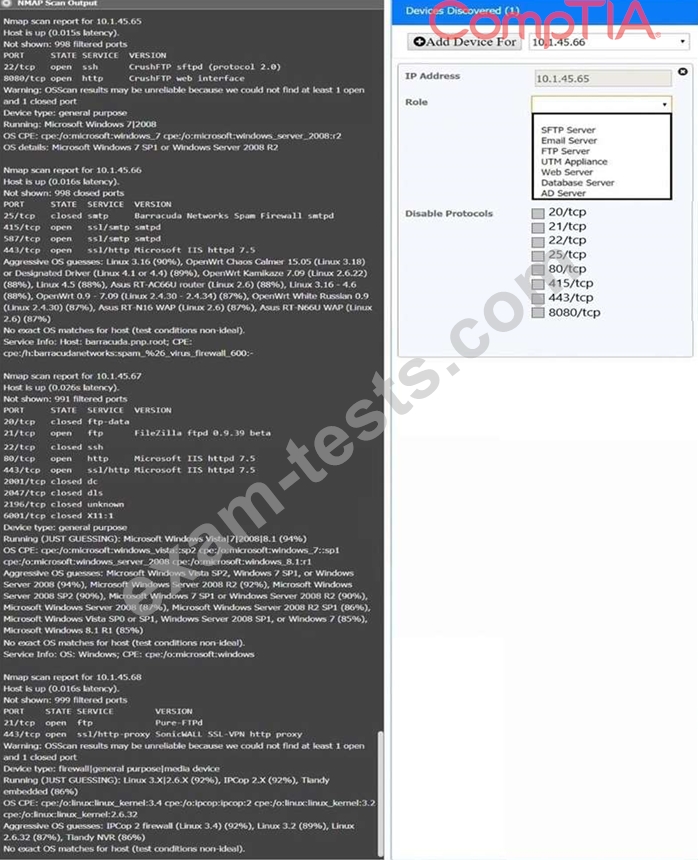
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only) The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines) If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with interpreting an Nmap scan output from company's privileged network.
The company's hardening guidelines indicate the following:
There should be one primary server or service per device.
Only default ports should be used.
Non-secure protocols should be disabled.
INSTRUCTIONS
Using the Nmap output, identify the devices on the network and their roles, and any open ports that should be closed.
For each device found by Nmap, add a device entry to the Devices Discovered list, with the following information:
The IP address of the device
The primary server or service of the device (Note that each IP should by associated with one service/port only) The protocol(s) that should be disabled based on the hardening guidelines (Note that multiple ports may need to be closed to comply with the hardening guidelines) If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 37
An organization's existing infrastructure includes site-to-site VPNs between datacenters. In the past year, a sophisticated attacker exploited a zero-day vulnerability on the VPN concentrator. Consequently, the Chief Information Security Officer (CISO) is making infrastructure changes to mitigate the risk of service loss should another zero-day exploit be used against the VPN solution.
Which of the following designs would be BEST for the CISO to use?
Which of the following designs would be BEST for the CISO to use?
Question 38
Which of the following protocols is a low power, low data rate that allows for the creation of PAN networks?
Question 39
A company suspects a web server may have been infiltrated by a rival corporation. The security engineer reviews the web server logs and finds the following:

The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:

Which of the following is an appropriate security control the company should implement?

The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:

Which of the following is an appropriate security control the company should implement?
Question 40
A cybersecurity engineer analyst a system for vulnerabilities. The tool created an OVAL. Results document as output. Which of the following would enable the engineer to interpret the results in a human readable form?
(Select TWO.)
(Select TWO.)
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

