Question 41
A security analyst is reading the results of a successful exploit that was recently conducted by third-party penetration testers. The testers reverse engineered a privileged executable. In the report, the planning and execution of the exploit is detailed using logs and outputs from the test However, the attack vector of the exploit is missing, making it harder to recommend remediation's. Given the following output:
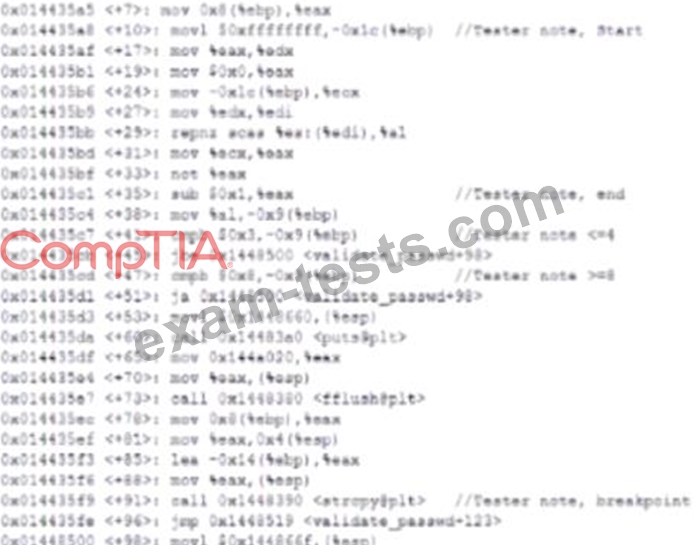
The penetration testers MOST likely took advantage of:

The penetration testers MOST likely took advantage of:
Question 42
Company A acquired Company B. During an audit, a security engineer found Company B's environment was inadequately patched. In response, Company A placed a firewall between the two environments until Company B's infrastructure could be integrated into Company A's security program.
Which of the following risk-handling techniques was used?
Which of the following risk-handling techniques was used?
Question 43
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
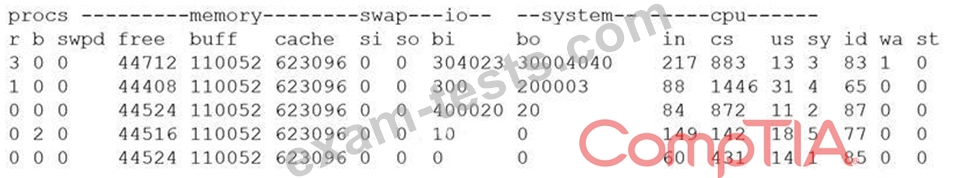
Based on the output above, from which of the following process IDs can the analyst begin an investigation?

Based on the output above, from which of the following process IDs can the analyst begin an investigation?
Question 44
An energy company is required to report the average pressure of natural gas used over the past quarter. A PLC sends data to a historian server that creates the required reports.
Which of the following historian server locations will allow the business to get the required reports in an OT and IT environment?
Which of the following historian server locations will allow the business to get the required reports in an OT and IT environment?
Question 45
An HVAC contractor requested network connectivity permission to remotely support/troubleshoot equipment issues at a company location. Currently, the company does not have a process that allows vendors remote access to the corporate network Which of the following solutions represents the BEST course of action to allow the contractor access?
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

