Question 21
A company suspects a web server may have been infiltrated by a rival corporation. The security engineer reviews the web server logs and finds the following:

The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:

Which of the following is an appropriate security control the company should implement?

The security engineer looks at the code with a developer, and they determine the log entry is created when the following line is run:

Which of the following is an appropriate security control the company should implement?
Question 22
A systems administrator is preparing to run a vulnerability scan on a set of information systems in the organization. The systems administrator wants to ensure that the targeted systems produce accurate information especially regarding configuration settings.
Which of the following scan types will provide the systems administrator with the MOST accurate information?
Which of the following scan types will provide the systems administrator with the MOST accurate information?
Question 23
An organization requires a contractual document that includes
* An overview of what is covered
* Goals and objectives
* Performance metrics for each party
* A review of how the agreement is managed by all parties
Which of the following BEST describes this type of contractual document?
* An overview of what is covered
* Goals and objectives
* Performance metrics for each party
* A review of how the agreement is managed by all parties
Which of the following BEST describes this type of contractual document?
Question 24
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

The security engineer looks at the UTM firewall rules and finds the following:
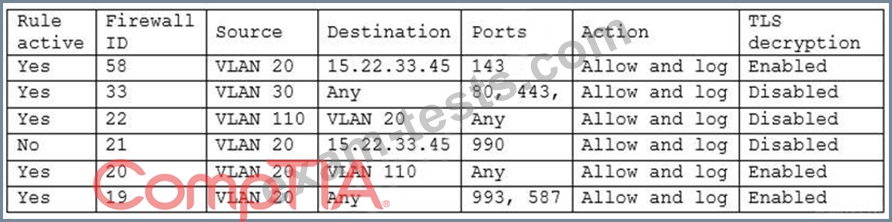
Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?

The security engineer looks at the UTM firewall rules and finds the following:

Which of the following should the security engineer do to ensure IMAPS functions properly on the corporate user network?
Question 25
A security architect is given the following requirements to secure a rapidly changing enterprise with an increasingly distributed and remote workforce
* Cloud-delivered services
* Full network security stack
* SaaS application security management
* Minimal latency for an optimal user experience
* Integration with the cloud 1AM platform
Which of the following is the BEST solution?
* Cloud-delivered services
* Full network security stack
* SaaS application security management
* Minimal latency for an optimal user experience
* Integration with the cloud 1AM platform
Which of the following is the BEST solution?
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

