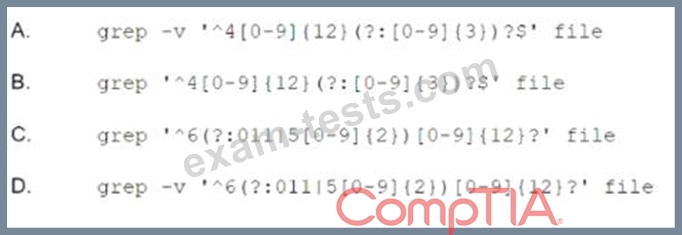
Question 26
An organization's finance system was recently attacked. A forensic analyst is reviewing the contents of the compromised files for credit card dat a. Which of the following commands should the analyst run to BEST determine whether financial data was lost?

Question 27
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?

Which of the following vulnerabilities does the code snippet resolve?
Question 28
A company launched a new service and created a landing page within its website network for users to access the service. Per company policy, all websites must utilize encryption for any authentication pages. A junior network administrator proceeded to use an outdated procedure to order new certificates. Afterward, customers are reporting the following error when accessing a new web page: NET:ERR_CERT_COMMON_NAME_INVALID. Which of the following BEST describes what the administrator should do NEXT?
Question 29
Based on PCI DSS v3.4, One Particular database field can store data, but the data must be unreadable. which of the following data objects meets this requirement?
Question 30
A company is implementing SSL inspection. During the next six months, multiple web applications that will be separated out with subdomains will be deployed.
Which of the following will allow the inspection of the data without multiple certificate deployments?
Which of the following will allow the inspection of the data without multiple certificate deployments?
Premium Bundle
Newest CAS-004 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-004 Exam! BraindumpsPass.com now offer the updated CAS-004 exam dumps, the BraindumpsPass.com CAS-004 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-004 pdf dumps with Exam Engine here:

