Question 226
Considering confidentiality and integrity, which of the following make servers more secure than desktops?
(Select THREE).
(Select THREE).
Question 227
A cybersecurity consultant is reviewing the following output from a vulnerability scan against a newly installed MS SQL Server 2012 that is slated to go into production in one week:
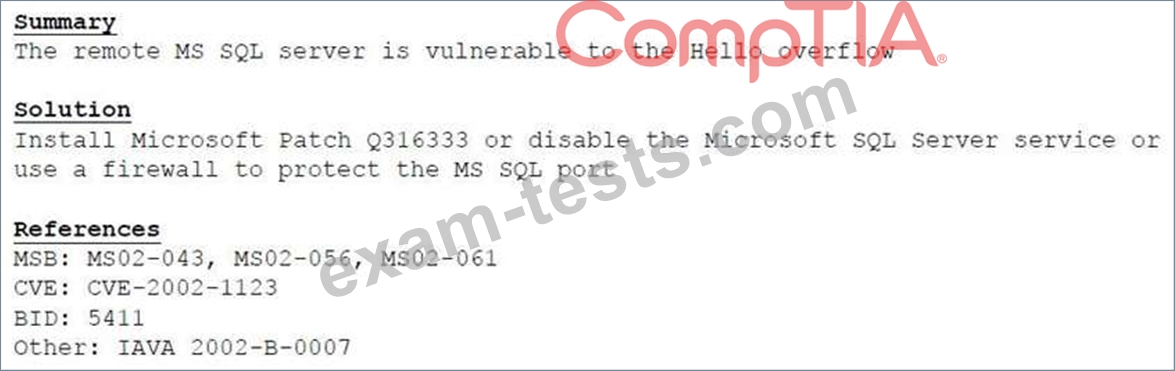
Based on the above information, which of the following should the system administrator do? (Select TWO).

Based on the above information, which of the following should the system administrator do? (Select TWO).
Question 228
A security professional is analyzing the results of a network utilization report. The report includes the following information:
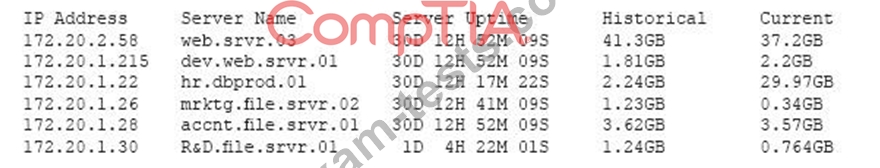
Which of the following servers needs further investigation?

Which of the following servers needs further investigation?
Question 229
Which of the following BEST describes why vulnerabilities found in ICS and SCADA can be difficult to remediate?
Question 230
A software assurance lab is performing a dynamic assessment on an application by automatically generating and inputting different, random data sets to attempt to cause an error/failure condition. Which of the following software assessment capabilities is the lab performing AND during which phase of the SDLC should this occur? (Select two.)

