Question 201
A business-critical application is unable to support the requirements in the current password policy because it does not allow the use of special characters. Management does not want to accept the risk of a possible security incident due to weak password standards. Which of the following is an appropriate means to limit the risks related to the application?
Question 202
During a recent audit, there were a lot of findings similar to and including the following:
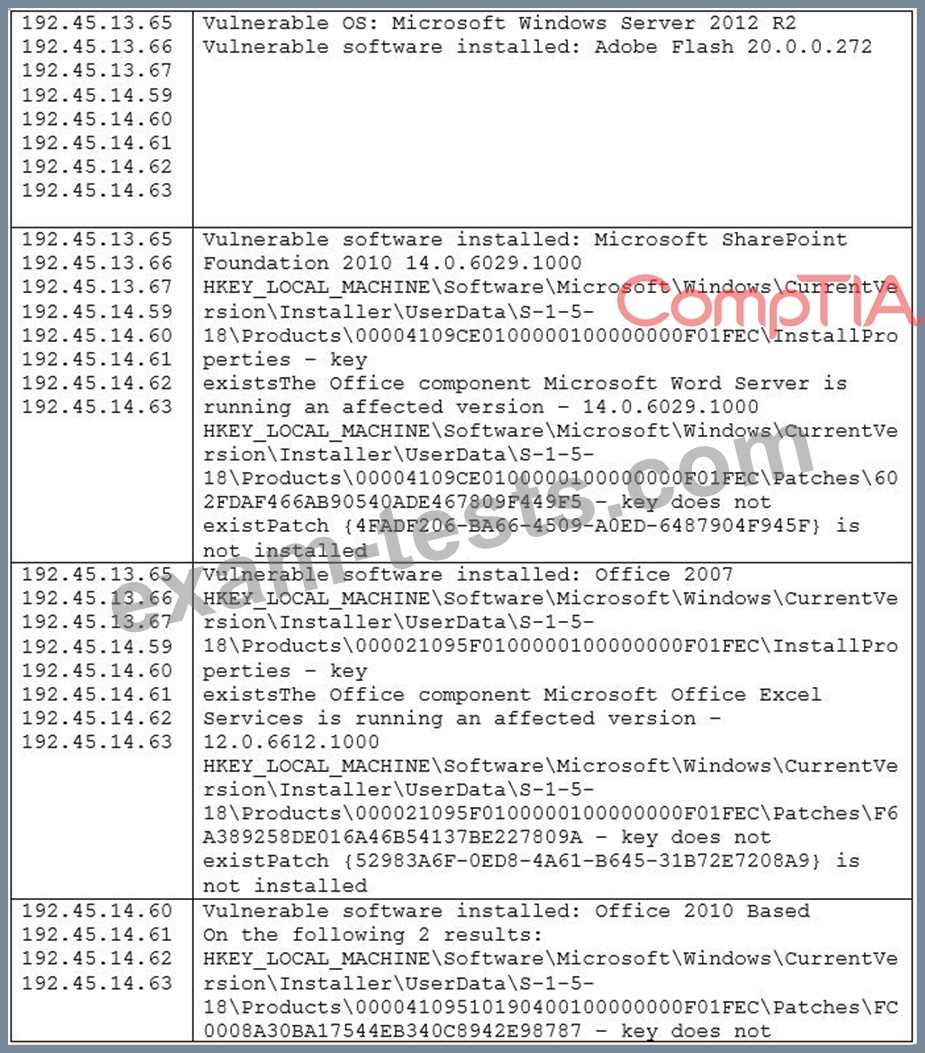
Which of the following would be the BEST way to remediate these findings and minimize similar findings in the future?

Which of the following would be the BEST way to remediate these findings and minimize similar findings in the future?
Question 203
A computer has been infected with a virus and is sending out a beacon to command and control server
through an unknown service. Which of the following should a security technician implement to drop the
traffic going to the command and control server and still be able to identify the infected host through
firewall logs?
through an unknown service. Which of the following should a security technician implement to drop the
traffic going to the command and control server and still be able to identify the infected host through
firewall logs?
Question 204
A security analyst is performing a forensic analysis on a machine that was the subject of some historic
SIEM alerts. The analyst noticed some network connections utilizing SSL on non-common ports, copies of
svchost.exe and cmd.exe in %TEMP% folder, and RDP files that had connected to external IPs. Which of
the following threats has the security analyst uncovered?
SIEM alerts. The analyst noticed some network connections utilizing SSL on non-common ports, copies of
svchost.exe and cmd.exe in %TEMP% folder, and RDP files that had connected to external IPs. Which of
the following threats has the security analyst uncovered?
Question 205
A cybersecurity analyst is currently investigating a server outage. The analyst has discovered the following value was entered for the username: 0xbfff601a. Which of the following attacks may be occurring?

