Question 191
A security analyst has performed various scans and found vulnerabilities in several applications that affect production data. Remediation of all exploits may cause certain applications to no longer work. Which of the following activities would need to be conducted BEFORE remediation?
Question 192
During the forensic phase of security investigation, it was discovered that an attacker was able to find private keys on a poorly secured team shared drive. The attacker used those keys to intercept and decrypt sensitive traffic on a web server. Which of the following describes this type of exploit and the potential remediation?
Question 193
When network administrators observe an increased amount of web traffic without an increased number of
financial transactions, the company is MOST likely experiencing which of the following attacks?
financial transactions, the company is MOST likely experiencing which of the following attacks?
Question 194
A company has received the results of an external vulnerability scan from its approved scanning vendor.
The company is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement
of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within
the time frame?
The company is required to remediate these vulnerabilities for clients within 72 hours of acknowledgement
of the scan results.
Which of the following contract breaches would result if this remediation is not provided for clients within
the time frame?
Question 195
Given the following log snippet:
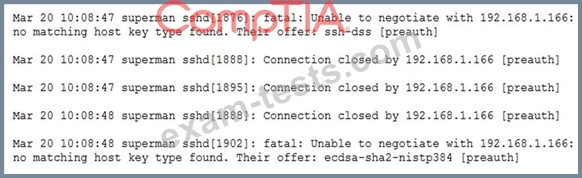
Which of the following describes the events that have occurred?

Which of the following describes the events that have occurred?

