Question 6
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team's NEXT step during the detection phase of this response process?
Question 7
A custom script currently monitors real-time logs of a SAMIL authentication server to mitigate brute-force attacks. Which of the following is a concern when moving authentication to a cloud service?
Question 8
A finance department employee has received a message that appears to have been sent from the Chief Financial Officer (CFO), asking the employee to perform a wire transfer. Analysis of the email shows the message came from an external source and is fraudulent. Which of the following would work BEST to improve the likelihood of employees quickly recognizing fraudulent emails?
Question 9
A company's domain has been spooled in numerous phishing campaigns. An analyst needs to determine the company is a victim of domain spoofing, despite having a DMARC record that should tell mailbox providers to ignore any email that fails DMARC upon review of the record, the analyst finds the following:
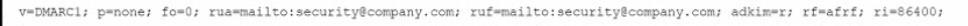
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
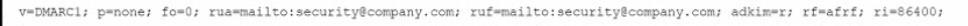
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
Question 10
It is important to parameterize queries to prevent:

