Question 21
A security analyst is monitoring authentication exchanges over the company's wireless network.
A sample of the Wireshark output is shown below:
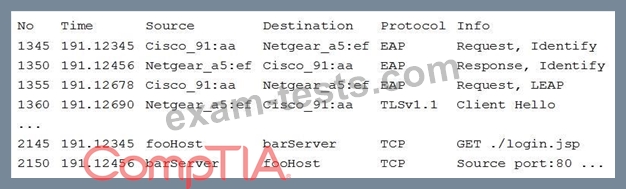
Which of the following would improve the security posture of the wireless network?
A sample of the Wireshark output is shown below:

Which of the following would improve the security posture of the wireless network?
Question 22
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following:

The analyst runs the following command next:
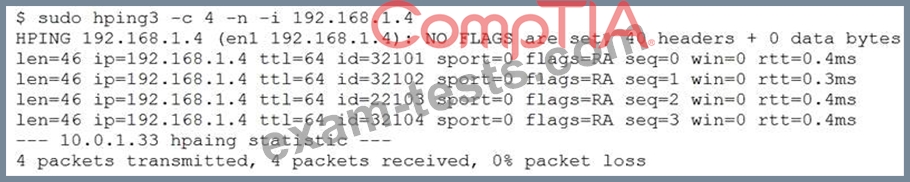
Which of the following would explain the difference in results?

The analyst runs the following command next:

Which of the following would explain the difference in results?
Question 23
Given the Nmap request below:
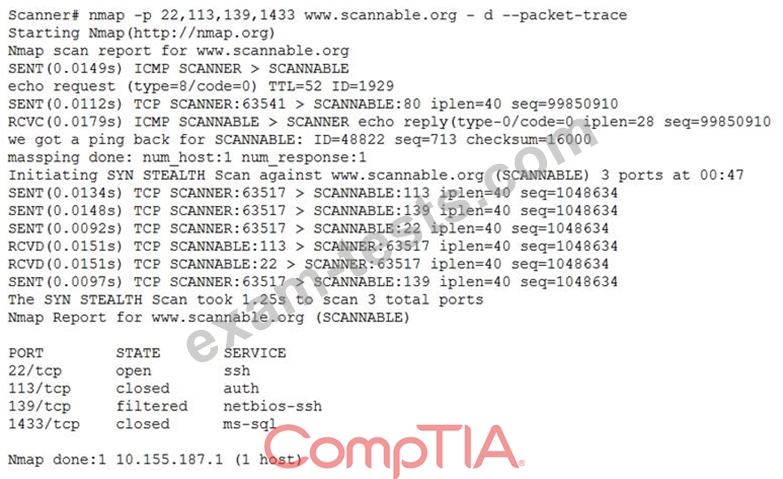
Which of the following actions will an attacker be able to initiate directly against this host?

Which of the following actions will an attacker be able to initiate directly against this host?
Question 24
A company wants to ensure a third party does not take intellectual property and build a competing product. Which of the following is a non-technical data and privacy control that would best protect the company?
Question 25
During an incident, a cybersecurity analyst found several entries in the web server logs that are related to an IP with a bad reputation . Which of the following would cause the analyst to further review the incident?
A)
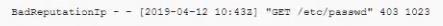
B)

C)

D)
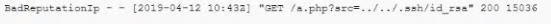
E)

A)
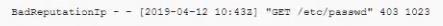
B)

C)

D)
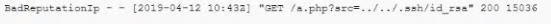
E)


