Question 11
A financial organization has offices located globally. Per the organization's policies and procedures, all executives who conduct Business overseas must have their mobile devices checked for malicious software or evidence of tempering upon their return. The information security department oversees the process, and no executive has had a device compromised. The Chief information Security Officer wants to Implement an additional safeguard to protect the organization's dat a. Which of the following controls would work BEST to protect the privacy of the data if a device is stolen?
Question 12
A company's marketing emails are either being found in a spam folder or not being delivered at all. The security analyst investigates the issue and discovers the emails in question are being sent on behalf of the company by a third party in1marketingpartners.com Below is the exiting SPP word:

Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)


Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)

Question 13
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has already identified active hosts in the network and is now scanning individual hosts to determine if any are running a web server. The output from the latest scan is shown below:
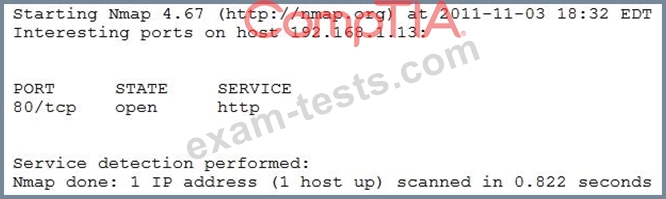
Which of the following commands would have generated the output above?

Which of the following commands would have generated the output above?
Question 14
A company's domain has been spooled in numerous phishing campaigns. An analyst needs to determine the company is a victim of domain spoofing, despite having a DMARC record that should tell mailbox providers to ignore any email that fails DMARC upon review of the record, the analyst finds the following:
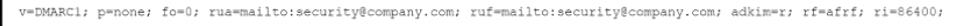
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
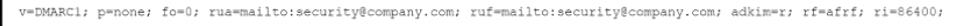
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
Question 15
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session.
Which of the following is the BEST technique to address the CISO's concerns?
Which of the following is the BEST technique to address the CISO's concerns?

