Question 271
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred:
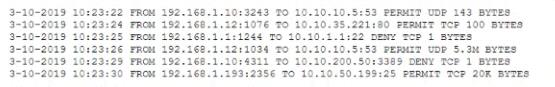
Which of the following IP addresses does the analyst need to investigate further?

Which of the following IP addresses does the analyst need to investigate further?
Question 272
After reading about data breaches at a competing company, senior leaders in an organization have grown increasingly concerned about social engineering attacks. They want to increase awareness among staff regarding this threat, but do not want to use traditional training methods because they regard these methods as ineffective. Which of the following approaches would BEST meet the requirements?
Question 273
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets.
Which of the following should be considered FIRST prior to disposing of the electronic data?
Which of the following should be considered FIRST prior to disposing of the electronic data?
Question 274
A security analyst is reviewing the following log from an email security service.
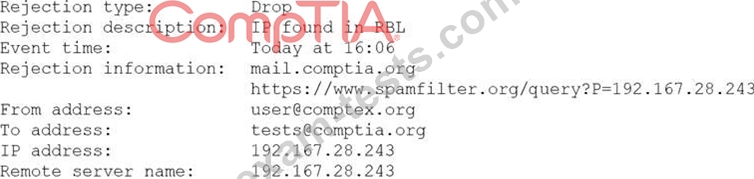
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 275
A company's Chief Information Security Officer (CISO) published an Internet usage policy that prohibits employees from accessing unauthorized websites. The IT department whitelisted websites used for business needs. The CISO wants the security analyst to recommend a solution that would improve security and support employee morale. Which of the following security recommendations would allow employees to browse non-business-related websites?

