Question 281
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
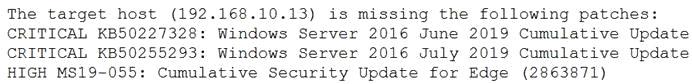
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Question 282
A security analyst is investigating a malware infection that occurred on a Windows system.
The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage.
The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
The system was not connected to a network and had no wireless capability Company policy prohibits using portable media or mobile storage.
The security analyst is trying to determine which user caused the malware to get onto the system.
Which of the following registry keys would MOST likely have this information?
Question 283
An analyst is conducting a log review and identifies the following snippet in one of the logs:
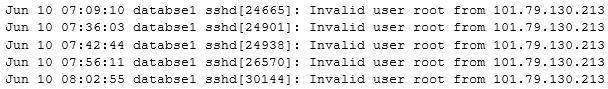
Which of the following MOST likely caused this activity?

Which of the following MOST likely caused this activity?
Question 284
A forensic analyst took an image of a workstation that was involved in an incident To BEST ensure the image is not tampered with me analyst should use:
Question 285
A security analyst has received reports of very slow, intermittent access to a public-facing corporate server.
Suspecting the system may be compromised, the analyst runs the following commands:
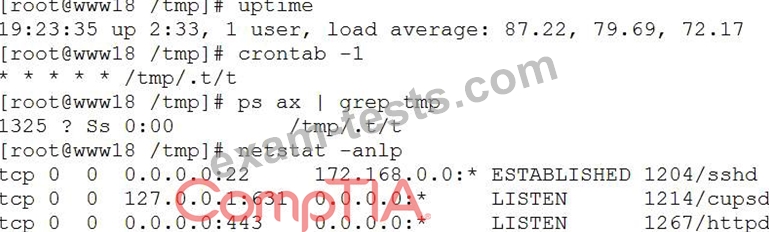
Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?
Suspecting the system may be compromised, the analyst runs the following commands:

Based on the output from the above commands, which of the following should the analyst do NEXT to further the investigation?

