Question 246
A security analyst needs to perform a search for connections with a suspicious IP on the network traffic. The company collects full packet captures at the Internet gateway and retains them for one week. Which of the following will enable the analyst to obtain the BEST results?
Question 247
A SIEM alert occurs with the following output:

Which of the following BEST describes this alert?

Which of the following BEST describes this alert?
Question 248
A system administrator is doing network reconnaissance of a company's external network to determine the vulnerability of various services that are running. Sending some sample traffic to the external host, the administrator obtains the following packet capture:
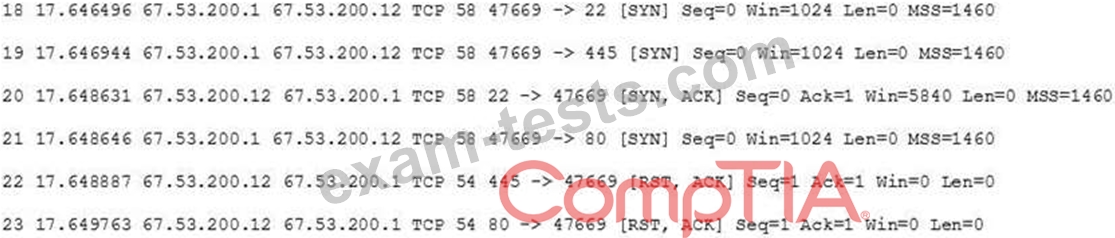
Based on the output, which of the following services should be further tested for vulnerabilities?

Based on the output, which of the following services should be further tested for vulnerabilities?
Question 249
In the development stage of the incident response policy, the security analyst needs to determine the stakeholders for the policy. Who of the following would be the policy stakeholders?
Question 250
A technician at a company's retail store notifies an analyst that disk space is being consumed at a rapid rate on several registers. The uplink back to the corporate office is also saturated frequently. The retail location has no Internet access. An analyst then observes several occasional IPS alerts indicating a server at corporate has been communicating with an address on a watchlist. Netflow data shows large quantities of data transferred at those times.
Which of the following is MOST likely causing the issue?
Which of the following is MOST likely causing the issue?

