Question 46
A cybersecurity analyst is reviewing log data and sees the output below:
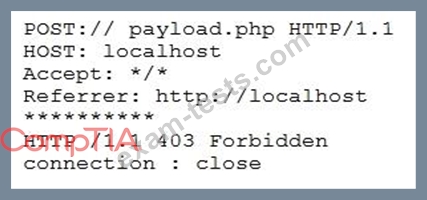
Which of the following technologies MOST likely generated this log?

Which of the following technologies MOST likely generated this log?
Question 47
Which of the following is a vulnerability that is specific to hypervisors?
Question 48
An information security analyst is compiling data from a recent penetration test and reviews the following output:
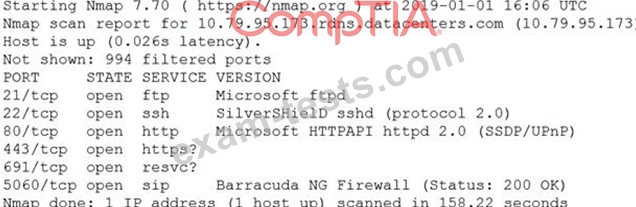
The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?

The analyst wants to obtain more information about the web-based services that are running on the target.
Which of the following commands would MOST likely provide the needed information?
Question 49
A user's computer has been running slowly when the user tries to access web pages. A security analyst runs the command netstat -aon from the command line and receives the following output:
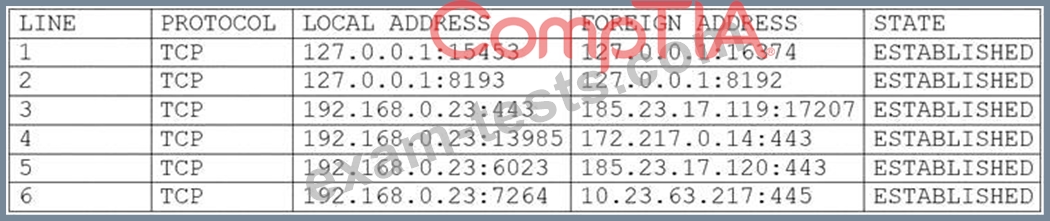
Which of the following lines indicates the computer may be compromised?

Which of the following lines indicates the computer may be compromised?
Question 50
The SFTP server logs show thousands of failed login attempts from hundreds of IP addresses worldwide. Which of the following controls would BEST protect the service?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

