Question 51
A cybersecurity analyst is contributing to a team hunt on an organization's endpoints.
Which of the following should the analyst do FIRST?
Which of the following should the analyst do FIRST?
Question 52
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team. Which of the following frameworks would BEST support the program? (Choose two.)
Question 53
After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a company's computer.
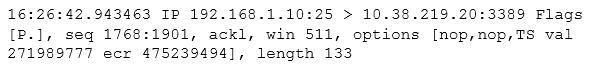
Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?

Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?
Question 54
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following:
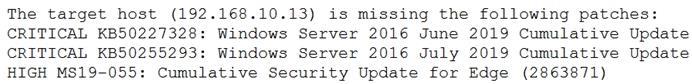
Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Tool A reported the following:

Tool B reported the following:

Which of the following BEST describes the method used by each tool? (Choose two.)
Question 55
Malicious users utilized brute force to access a system. An analyst is investigating these attacks and recommends methods to management that would help secure the system. Which of the following controls should the analyst recommend? (Choose three.)
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

