Question 76
A security analyst at a small regional bank has received an alert that nation states are attempting to infiltrate financial institutions via phishing campaigns. Which of the following techniques should the analyst recommend as a proactive measure to defend against this type of threat?
Question 77
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.
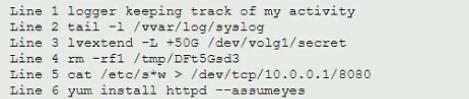
Which of the following commands should the analyst investigate FIRST?

Which of the following commands should the analyst investigate FIRST?
Question 78
Company A's security policy states that only PKI authentication should be used for all SSH accounts. A security analyst from Company A is reviewing the following auth.log and configuration settings:
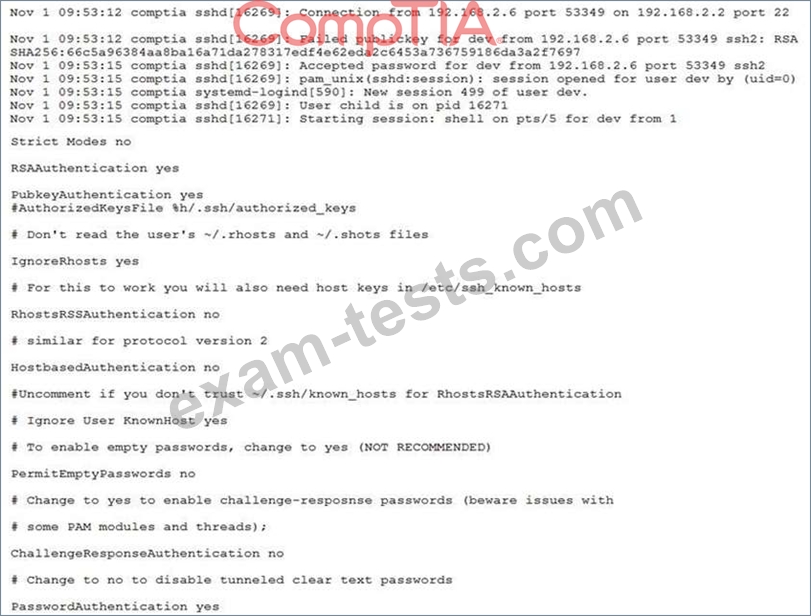
Which of the following changes should be made to the following sshd_config file to establish compliance with the policy?

Which of the following changes should be made to the following sshd_config file to establish compliance with the policy?
Question 79
A security analyst is investigating an incident that appears to have started with SOL injection against a publicly available web application. Which of the following is the FIRST step the analyst should take to prevent future attacks?
Question 80
A cybersecurity analyst has several log files to review. Instead of using grep and cat commands, the analyst decides to find a better approach to analyze the logs. Given a list of tools, which of the following would provide a more efficient way for the analyst to conduct a timeline analysis, do keyword searches, and output a report?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

