Question 91
A company was recently awarded several large government contracts and wants to determine its current risk from one specific APT.
Which of the following threat modeling methodologies would be the MOST appropriate to use during this analysis?
Which of the following threat modeling methodologies would be the MOST appropriate to use during this analysis?
Question 92
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity. Below is a snippet of the log:
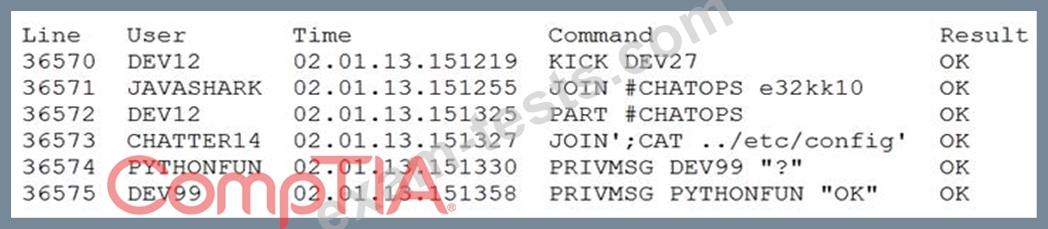
Which of the following commands would work BEST to achieve the desired result?

Which of the following commands would work BEST to achieve the desired result?
Question 93
A Chief Information Security Officer (CISO) wants to upgrade an organization's security posture by improving proactive activities associated with attacks from internal and external threats.
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
Which of the following is the MOST proactive tool or technique that feeds incident response capabilities?
Question 94
After completing a vulnerability scan, the following output was noted:
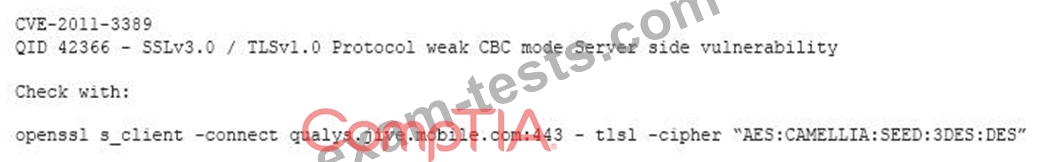
Which of the following vulnerabilities has been identified?

Which of the following vulnerabilities has been identified?
Question 95
An audit has revealed an organization is utilizing a large number of servers that are running unsupported operating systems.
As part of the management response phase of the audit, which of the following would BEST demonstrate senior management is appropriately aware of and addressing the issue?
As part of the management response phase of the audit, which of the following would BEST demonstrate senior management is appropriately aware of and addressing the issue?

