Question 151
A server contains baseline images that are deployed to sensitive workstations on a regular basis.
The images are evaluated once per month for patching and other fixes, but do not change otherwise. Which of the following controls should be put in place to secure the file server and ensure the images are not changed?
The images are evaluated once per month for patching and other fixes, but do not change otherwise. Which of the following controls should be put in place to secure the file server and ensure the images are not changed?
Question 152
The Chief Information Security Officer (CISO) asked for a topology discovery to be conducted and verified against the asset inventory. The discovery is failing and not providing reliable or complete data. The syslog shows the following information:
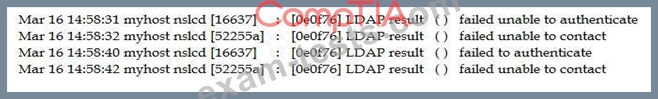
Which of the following describes the reason why the discovery is failing?

Which of the following describes the reason why the discovery is failing?
Question 153
A cybersecurity analyst is currently using Nessus to scan several FTP servers. Upon receiving the results of the scan, the analyst needs to further test to verify that the vulnerability found exists.
The analyst uses the following snippet of code:
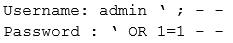
Which of the following vulnerabilities is the analyst checking for?
The analyst uses the following snippet of code:

Which of the following vulnerabilities is the analyst checking for?
Question 154
The help desk provided a security analyst with a screenshot of a user's desktop:
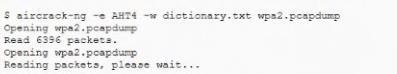
For which of the following is aircrack-ng being used?

For which of the following is aircrack-ng being used?
Question 155
During a routine log review, a security analyst has found the following commands that cannot be identified from the Bash history log on the root user.

Which of the following commands should the analyst investigate FIRST?

Which of the following commands should the analyst investigate FIRST?

