Question 146
An analyst performs a routine scan of a host using Nmap and receives the following output:
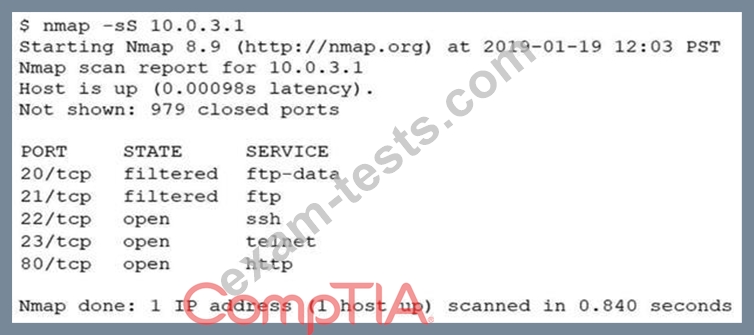
Which of the following should the analyst investigate FIRST?

Which of the following should the analyst investigate FIRST?
Question 147
A system administrator has reviewed the following output:
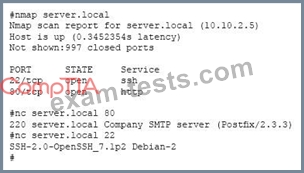
Which of the following can a system administrator infer from the above output?

Which of the following can a system administrator infer from the above output?
Question 148
A security analyst is reviewing the following log from an email security service.
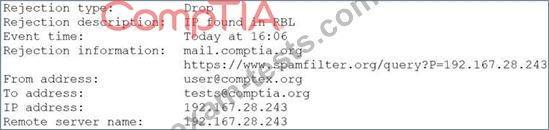
Which of the following BEST describes the reason why the email was blocked?

Which of the following BEST describes the reason why the email was blocked?
Question 149
A security analyst inspects the header of an email that is presumed to be malicious and sees the following:
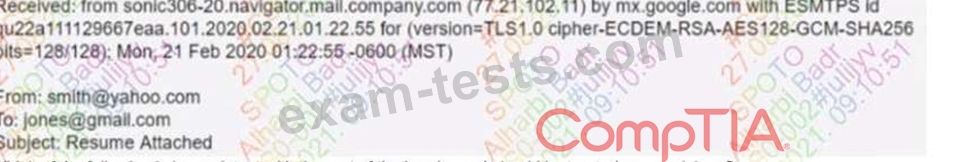
Which of the following is inconsistent with the rest of the header and should be treated as suspicious?

Which of the following is inconsistent with the rest of the header and should be treated as suspicious?
Question 150
While analyzing logs from a WAF, a cybersecurity analyst finds the following:
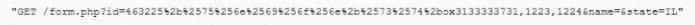
Which of the following BEST describes what the analyst has found?
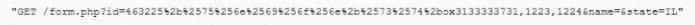
Which of the following BEST describes what the analyst has found?

