Question 166
An analyst performs a routine scan of a host using Nmap and receives the following output:
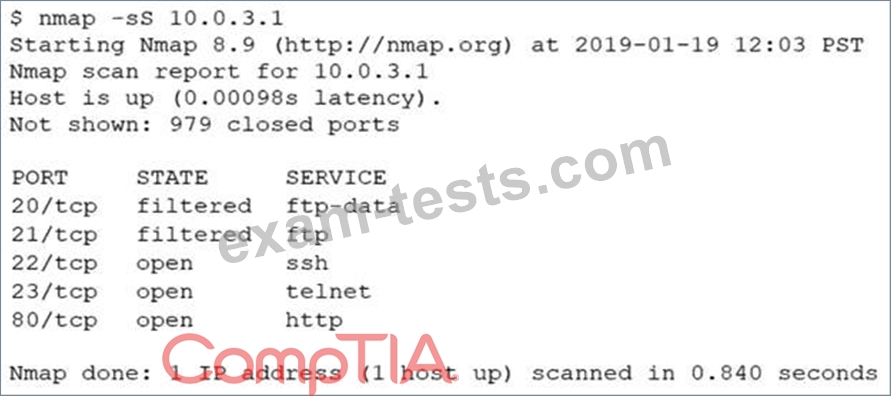
Which of the following should the analyst investigate FIRST?

Which of the following should the analyst investigate FIRST?
Question 167
A company has been a victim of multiple volumetric DoS attacks. Packet analysis of the offending traffic shows the following:

Which of the following mitigation techniques is MOST effective against the above attack?

Which of the following mitigation techniques is MOST effective against the above attack?
Question 168
An organization that uses SPF has been notified emails sent via its authorized third-party partner are getting rejected A security analyst reviews the DNS entry and sees the following:
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com -all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com -all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
Question 169
A company's marketing emails are either being found in a spam folder or not being delivered at all. The security analyst investigates the issue and discovers the emails in question are being sent on behalf of the company by a third party in1marketingpartners.com Below is the exiting SPP word:

Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)
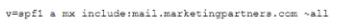

Which of the following updates to the SPF record will work BEST to prevent the emails from being marked as spam or blocked?
A)

B)

C)

D)
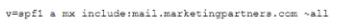
Question 170
Joe, a penetration tester, used a professional directory to identify a network administrator and ID administrator for a client's company. Joe then emailed the network administrator, identifying himself as the ID administrator, and asked for a current password as part of a security exercise. Which of the following techniques were used in this scenario?
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

