Question 71
A security analyst is reviewing the logs from an internal chat server. The chat.log file is too large to review manually, so the analyst wants to create a shorter log file that only includes lines associated with a user demonstrating anomalous activity. Below is a snippet of the log:
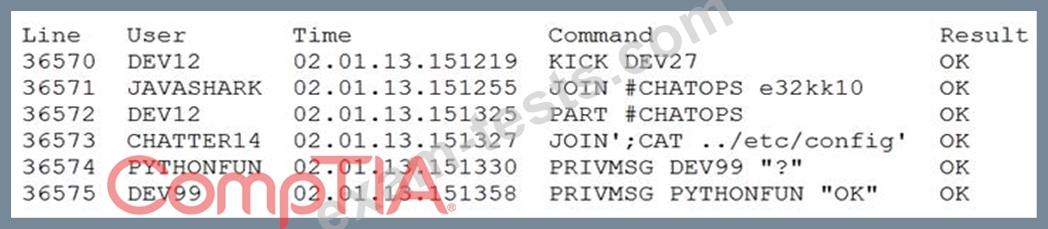
Which of the following commands would work BEST to achieve the desired result?

Which of the following commands would work BEST to achieve the desired result?
Question 72
To prioritize the morning's work, an analyst is reviewing security alerts that have not yet been investigated. Which of the following assets should be investigated FIRST?
Question 73
A security analyst discovers suspicious host activity while performing monitoring activities. The analyst pulls a packet capture for the activity and sees the following:

Which of the following describes what has occurred?

Which of the following describes what has occurred?
Question 74
An organization's network administrator uncovered a rogue device on the network that is emulating the charactenstics of a switch. The device is trunking protocols and inserting tagging va
the flow of traffic at the data link layer
Which of the following BEST describes this attack?
the flow of traffic at the data link layer
Which of the following BEST describes this attack?
Question 75
A security analyst working in the SOC recently discovered Balances m which hosts visited a specific set of domains and IPs and became infected with malware. Which of the following is the MOST appropriate action to take in the situation?

