Question 76
While investigating reports or issues with a web server, a security analyst attempts to log in remotely and recedes the following message:
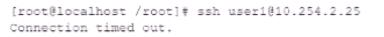
The analyst accesses the server console, and the following console messages are displayed:

The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:
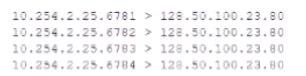
Which of the following is the BEST step for the analyst to lake next in this situation?
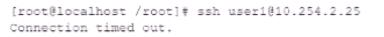
The analyst accesses the server console, and the following console messages are displayed:

The analyst is also unable to log in on the console. While reviewing network captures for the server, the analyst sees many packets with the following signature:

Which of the following is the BEST step for the analyst to lake next in this situation?
Question 77
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content Which of the following is the NEXT step the analyst should take?
Question 78
An incident responder successfully acquired application binaries off a mobile device for later forensic analysis.
Which of the following should the analyst do NEXT?
Which of the following should the analyst do NEXT?
Question 79
While implementing a PKI for a company, a security analyst plans to utilize a dedicated server as the certAcate authority that is only used to sign intermediate certificates. Which of the following are the MOST secure states for the certificate authority server when it is not in use? (Select TWO)
Question 80
Which of the following BEST explains the function of a managerial control?

