Question 1
A company is moving from the use of web servers hosted in an internal datacenter to a containerized cloud platform. An analyst has been asked to identify indicators of compromise in the containerized environment. Which of the following would BEST indicate a running container has been compromised?
Question 2
Which of the following is the use of tools to simulate the ability for an attacker to gain access to a specified network?
Question 3
A company's domain has been spooled in numerous phishing campaigns. An analyst needs to determine the company is a victim of domain spoofing, despite having a DMARC record that should tell mailbox providers to ignore any email that fails DMARC upon review of the record, the analyst finds the following:
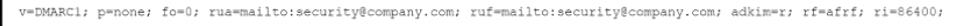
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
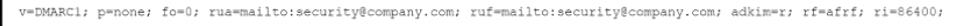
Which of the following BEST explains the reason why the company's requirements are not being processed correctly by mailbox providers?
Question 4
A small business does not have enough staff in the accounting department to segregate duties. The controller writes the checks for the business and reconciles them against the ledger. To ensure there is no fraud occurring, the business conducts quarterly reviews in which a different officer in the business compares all the cleared checks against the ledger. Which of the following BEST describes this type of control?
Question 5
Which of the following attacks can be prevented by using output encoding?

