Question 6
A finance department employee has received a message that appears to have been sent from the Chief Financial Officer (CFO) asking the employee to perform a wife transfer Analysis of the email shows the message came from an external source and is fraudulent. Which of the following would work BEST to improve the likelihood of employees quickly recognizing fraudulent emails?
Question 7
An information security analyst observes anomalous behavior on the SCADA devices in a power plant. This behavior results in the industrial generators overheating and destabilizing the power supply.
Which of the following would BEST identify potential indicators of compromise?
Which of the following would BEST identify potential indicators of compromise?
Question 8
A security analyst is reviewing vulnerability scan results and notices new workstations are being flagged as having outdated antivirus signatures. The analyst observes the following plugin output:

The analyst uses the vendor's website to confirm the oldest supported version is correct. Which of the following BEST describes the situation?

The analyst uses the vendor's website to confirm the oldest supported version is correct. Which of the following BEST describes the situation?
Question 9
After a breach involving the exfiltration of a large amount of sensitive data a security analyst is reviewing the following firewall logs to determine how the breach occurred:
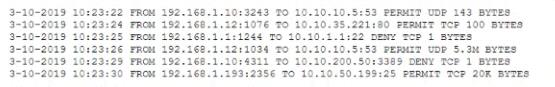
Which of the following IP addresses does the analyst need to investigate further?

Which of the following IP addresses does the analyst need to investigate further?
Question 10
Which of the following are components of the intelligence cycle? (Select TWO.)
Premium Bundle
Newest CS0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CS0-002 Exam! BraindumpsPass.com now offer the updated CS0-002 exam dumps, the BraindumpsPass.com CS0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CS0-002 pdf dumps with Exam Engine here:

