Question 21
Which two configuration settings are synchronized when FortiGate devices are in an active-active HA cluster? (Choose two.)
Question 22
Refer to the exhibit.
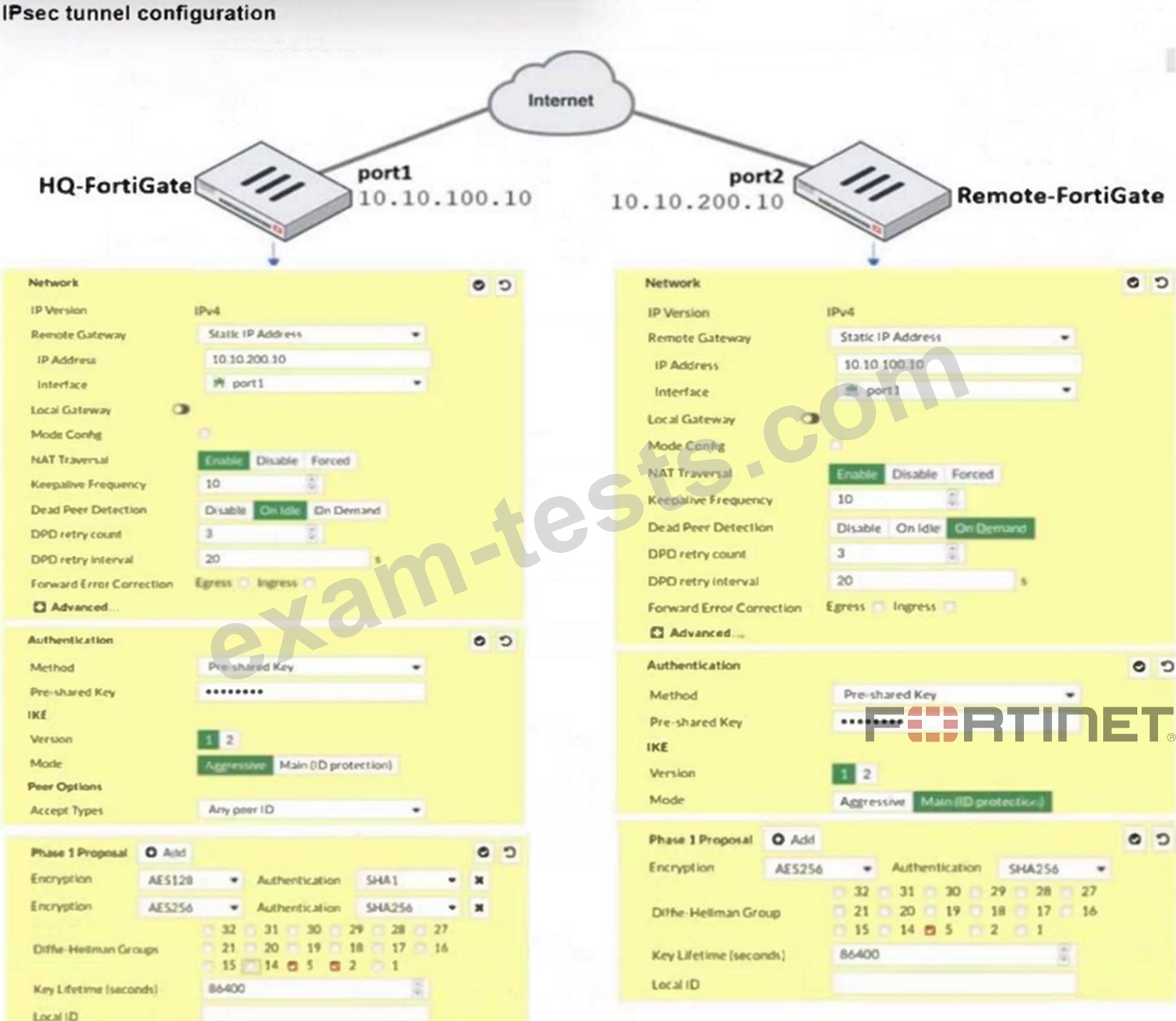
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)

A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
Question 23
Refer to the exhibit.
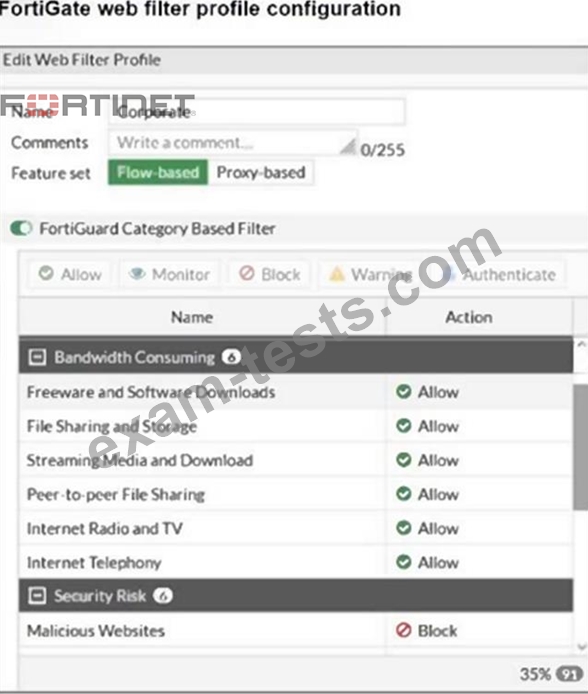
The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)

The exhibit shows the FortiGuard Category Based Filter section of a corporate web filter profile.
An administrator must block access to download.com, which belongs to the Freeware and Software Downloads category. The administrator must also allow other websites in the same category.
What are two solutions for satisfying the requirement? (Choose two.)
Question 24
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.
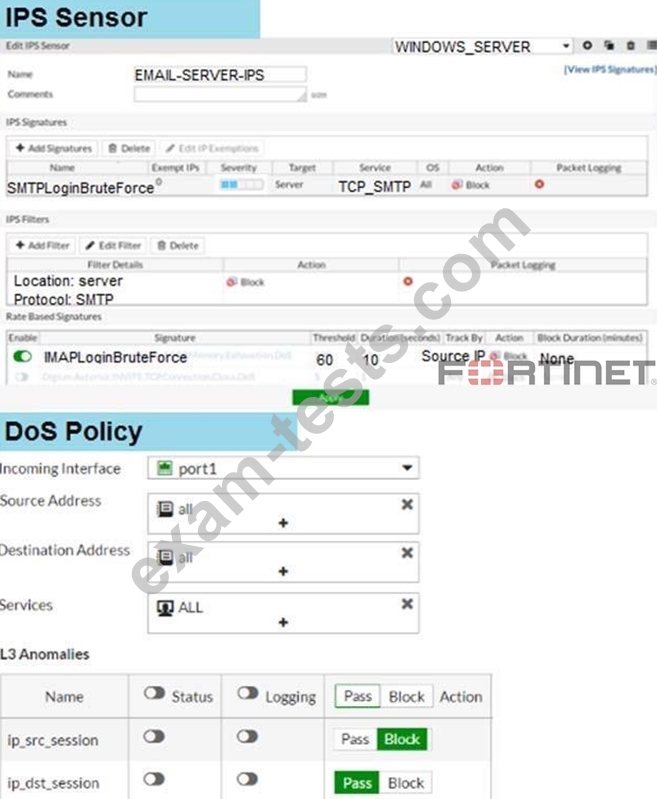
When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?

When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?
Question 25
Refer to the exhibit to view the application control profile.
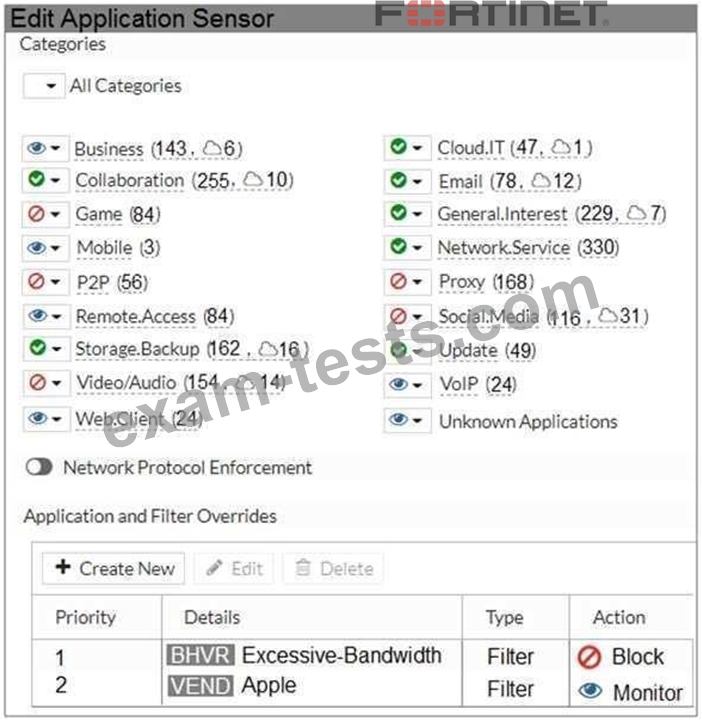
Users who use Apple FaceTime video conferences are unable to set up meetings.
In this scenario, which statement is true?

Users who use Apple FaceTime video conferences are unable to set up meetings.
In this scenario, which statement is true?

