Question 36
To complete the final step of a Security Fabric configuration, an administrator must authorize all the devices on which device?
Question 37
Refer to the exhibit.
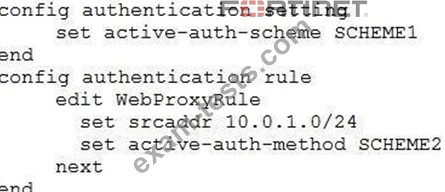
The exhibit shows a FortiGate configuration.
How does FortiGate handle web proxy traffic coming from the IP address 10.2.1.200, that requires authorization?

The exhibit shows a FortiGate configuration.
How does FortiGate handle web proxy traffic coming from the IP address 10.2.1.200, that requires authorization?
Question 38
Refer to the exhibit.

The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)

The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
Question 39
Refer to the exhibit.

FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt.
What is the most likely reason for this situation?

FortiGate is configured for firewall authentication. When attempting to access an external website, the user is not presented with a login prompt.
What is the most likely reason for this situation?
Question 40
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?

