Question 31
Which two statements describe how the RPF check is used? (Choose two.)
Question 32
View the exhibit.
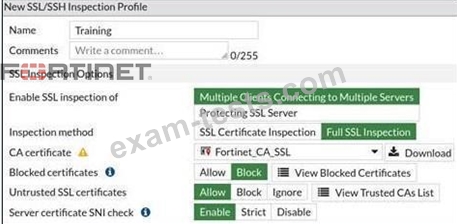
Which two behaviors result from this full (deep) SSL configuration? (Choose two.)

Which two behaviors result from this full (deep) SSL configuration? (Choose two.)
Question 33
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
Question 34
Which three statements are true regarding session-based authentication? (Choose three.)
Question 35
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
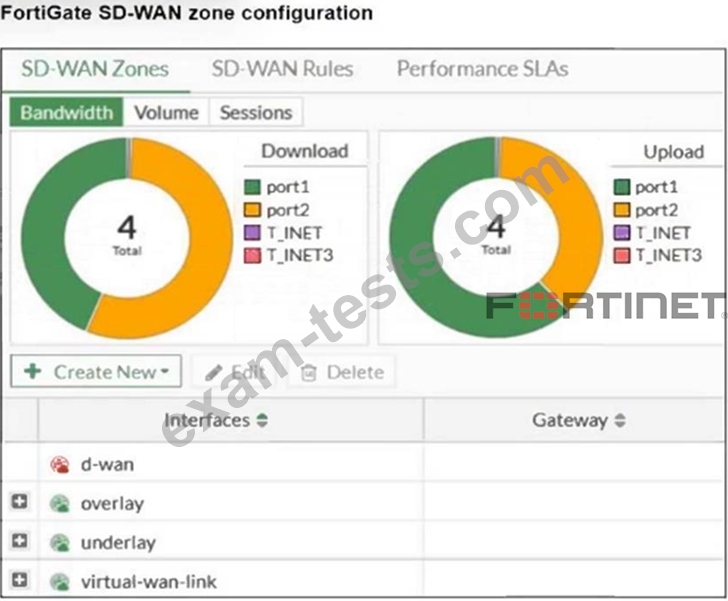
Based on the exhibit, which statement is true?

Based on the exhibit, which statement is true?

