Question 1
Which statement is true about certificate OCSP and CRL technology?
Question 2
The firewall uses display diagnostic-information to collect system diagnostic information in the diagnosis view, but cannot obtain the information output by which of the following commands?
Question 3
A company has the following requirements:
The intranet users in the Trust area are on the 192.160.1.0/24 network segment and can access the Internet.
Which of the following configurations are correct:
traffic-policy
profile trust_tountrust
bandwidth downstream
maximum-bandwidth 400000
bandwidth downstream
guaranteed-bandwidth 50000
bandwidth ip-car downstream
maximum-bandwidth per-ip 2000
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 192.160.1.0 24
action qos profile
trust_to_untrust
#
The intranet users in the Trust area are on the 192.160.1.0/24 network segment and can access the Internet.
Which of the following configurations are correct:
traffic-policy
profile trust_tountrust
bandwidth downstream
maximum-bandwidth 400000
bandwidth downstream
guaranteed-bandwidth 50000
bandwidth ip-car downstream
maximum-bandwidth per-ip 2000
rule name trust_to_untrust
source-zone trust
destination-zone untrust
source-address 192.160.1.0 24
action qos profile
trust_to_untrust
#

Question 4
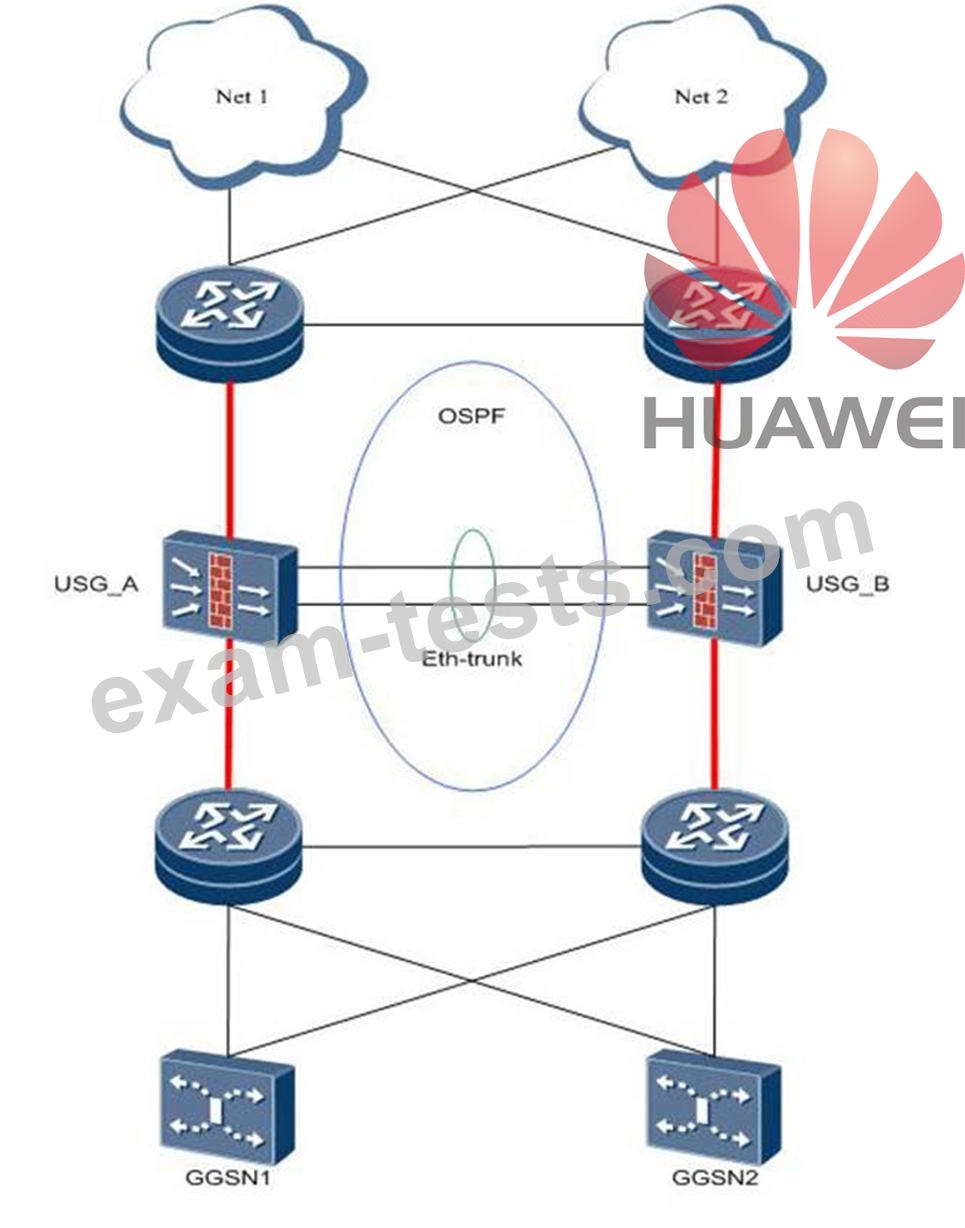
In the dual-system hot-standby network, the service interface works at Layer 3, the upstream and downstream are connected to the router, the firewall and the upstream and downstream run an OSPF process, which provides the dual-system hot-standby burden sharing network, and the firewall provides the NAT function. The following Incorrect planning deployment advice:

Question 5
For some large IP data packets, in order to meet the requirements of the MTU (Maximum Transmission Unit) of the link layer, it needs to be fragmented and divided into several IP packets during the transmission process. In each IP header there is an offset field and a split flag (MF), where the offset field indicates the location of the fragment in the entire IP packet. If the attacker sets the offset field to an incorrect value after intercepting the IP data packet, the receiver cannot correctly combine the values of the offset field in the data packet after receiving the split data packets. In this way, the receiver will keep trying, and the operating system will crash due to resource exhaustion.
What is this attack method?
What is this attack method?

