- Home
- PECB Certification
- ISO-IEC-27001-Lead-Auditor-CN Exam
- PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166 Practice Test
Question 131
審計小組負責人正計劃在今年稍早完成第三方監督審計後進行後續審計。他們決定在考慮採取糾正措施之前先驗證需要糾正的不合格項。
根據以下的描述,下列哪四項是監督中發現的不合格項的修正?
根據以下的描述,下列哪四項是監督中發現的不合格項的修正?
Correct Answer: A,B,C,E
According to the PECB Candidate Handbook for ISO/IEC 27001 Lead Auditor, a correction is an action to eliminate a detected nonconformity, such as rework, repair, or replacement1. The examples of A, B, C, and E are corrections because they fix the errors or defects that caused the nonconformities, such as a missing signature, a missing guide, a wrong date, or a wrong colour code. The other examples (D, F, G, and H) are not corrections, but corrective actions, because they address the root causes of the nonconformities, such as inadequate training, poor planning, ineffective documentation, or unclear responsibility2. Reference: 1: PECB Candidate Handbook for ISO/IEC 27001 Lead Auditor, page 35, section 4.5.12: PECB Candidate Handbook for ISO/IEC 27001 Lead Auditor, page 36, section 4.5.2.
Question 132
當審核團隊的另一位成員向您尋求澄清時,您正在進行第三方監督審核。他們被要求評估組織對控制 5.7 - 威脅情報的應用。他們知道這是 2022 年版 ISO/IEC 中引入的新控制措施之一
27001,他們希望確保正確審核控制。
他們準備了一份清單來協助他們進行審核,並希望您確認他們計劃的活動符合控制要求。
下列哪三個選項代表有效的審計追蹤?
27001,他們希望確保正確審核控制。
他們準備了一份清單來協助他們進行審核,並希望您確認他們計劃的活動符合控制要求。
下列哪三個選項代表有效的審計追蹤?
Correct Answer: A,D,F
According to ISO/IEC 27001:2022, which specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS), control 5.7 requires an organization to establish and maintain a threat intelligence process to identify and evaluate information security threats that are relevant to its ISMS scope and objectives1. The organization should use internal and external sources of information, such as vulnerability databases, threat feeds, industry reports, etc., to produce threat intelligence that can be used to support risk assessment and treatment, as well as other information security activities1. Therefore, when auditing the organization's application of control 5.7, an ISMS auditor should verify that these aspects are met in accordance with the audit criteria.
Three options that represent valid audit trails for verifying control 5.7 are:
I will review the organisation's threat intelligence process and will ensure that this is fully documented: This option is valid because it can provide evidence of how the organization has established and maintained a threat intelligence process that is consistent with its ISMS scope and objectives. It can also verify that the process is documented according to clause 7.5 of ISO/IEC 27001:20221.
I will check that threat intelligence is actively used to protect the confidentiality, integrity and availability of the organisation's information assets: This option is valid because it can provide evidence of how the organization has used threat intelligence to support its risk assessment and treatment, as well as other information security activities, such as incident response, awareness, or monitoring. It can also verify that the organization has achieved its information security objectives according to clause 6.2 of ISO/IEC 27001:20221.
I will determine whether internal and external sources of information are used in the production of threat intelligence: This option is valid because it can provide evidence of how the organization has used various sources of information, such as vulnerability databases, threat feeds, industry reports, etc., to produce threat intelligence that is relevant and reliable. It can also verify that the organization has complied with the requirement of control 5.7 of ISO/IEC 27001:20221.
The other options are not valid audit trails for verifying control 5.7, as they are not related to the control or its requirements. For example:
I will speak to top management to make sure all staff are aware of the importance of reporting threats: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may be related to another control or requirement regarding information security awareness or communication, but not specifically to control 5.7.
I will ensure that the task of producing threat intelligence is assigned to the organisation s internal audit team: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also contradict the requirement for auditor independence and objectivity, as recommended by ISO 19011:20182, which provides guidelines for auditing management systems.
I will ensure that the organisation's risk assessment process begins with effective threat intelligence: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also imply a prescriptive approach to risk assessment that is not consistent with ISO/IEC 27005:20183, which provides guidelines for information security risk management.
I will review how information relating to information security threats is collected and evaluated to produce threat intelligence: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also be too vague or broad to be an effective audit trail, as it does not specify what criteria or methods are used for collecting and evaluating information.
I will ensure that appropriate measures have been introduced to inform top management as to the effectiveness of current threat intelligence arrangements: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may be related to another control or requirement regarding management review or performance evaluation, but not specifically to control 5.7.
Three options that represent valid audit trails for verifying control 5.7 are:
I will review the organisation's threat intelligence process and will ensure that this is fully documented: This option is valid because it can provide evidence of how the organization has established and maintained a threat intelligence process that is consistent with its ISMS scope and objectives. It can also verify that the process is documented according to clause 7.5 of ISO/IEC 27001:20221.
I will check that threat intelligence is actively used to protect the confidentiality, integrity and availability of the organisation's information assets: This option is valid because it can provide evidence of how the organization has used threat intelligence to support its risk assessment and treatment, as well as other information security activities, such as incident response, awareness, or monitoring. It can also verify that the organization has achieved its information security objectives according to clause 6.2 of ISO/IEC 27001:20221.
I will determine whether internal and external sources of information are used in the production of threat intelligence: This option is valid because it can provide evidence of how the organization has used various sources of information, such as vulnerability databases, threat feeds, industry reports, etc., to produce threat intelligence that is relevant and reliable. It can also verify that the organization has complied with the requirement of control 5.7 of ISO/IEC 27001:20221.
The other options are not valid audit trails for verifying control 5.7, as they are not related to the control or its requirements. For example:
I will speak to top management to make sure all staff are aware of the importance of reporting threats: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may be related to another control or requirement regarding information security awareness or communication, but not specifically to control 5.7.
I will ensure that the task of producing threat intelligence is assigned to the organisation s internal audit team: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also contradict the requirement for auditor independence and objectivity, as recommended by ISO 19011:20182, which provides guidelines for auditing management systems.
I will ensure that the organisation's risk assessment process begins with effective threat intelligence: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also imply a prescriptive approach to risk assessment that is not consistent with ISO/IEC 27005:20183, which provides guidelines for information security risk management.
I will review how information relating to information security threats is collected and evaluated to produce threat intelligence: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may also be too vague or broad to be an effective audit trail, as it does not specify what criteria or methods are used for collecting and evaluating information.
I will ensure that appropriate measures have been introduced to inform top management as to the effectiveness of current threat intelligence arrangements: This option is not valid because it does not provide evidence of how the organization has established and maintained a threat intelligence process or used threat intelligence to support its ISMS activities. It may be related to another control or requirement regarding management review or performance evaluation, but not specifically to control 5.7.
Question 133
下列哪一項是組織環境的定義?
Correct Answer: C
The context of the organisation is the business environment in which the organisation operates and defines its information security management system (ISMS). It includes the internal and external factors and conditions that can influence the organisation's information security objectives, strategies, and policies. The context of the organisation helps the organisation to identify the scope, boundaries, and requirements of the ISMS, as well as the interested parties and their expectations. The context of the organisation is determined by considering both internal and external issues, such as the organisational structure, culture, values, mission, vision, objectives, strategies, resources, capabilities, processes, activities, products, services, markets, customers, competitors, suppliers, partners, regulators, laws, regulations, standards, guidelines, best practices, risks, opportunities, threats, vulnerabilities, etc. Reference: ISO 27001:2022 Clause 4 Context of the organization, ISO 27001 Requirement 4.1 - Understanding the Context of the Organisation, ISO 27001 context of the organization - How to define it - Advisera
Question 134
使用審計測試計劃組合的目的是什麼?
Correct Answer: A
Comprehensive and Detailed In-Depth
A . Correct Answer:
Combining multiple audit test plans ensures different perspectives and validation techniques are applied, improving audit accuracy.
ISO 19011:2018 encourages a diversified approach to auditing to ensure comprehensive results.
B . Incorrect:
Not all areas require equal auditing-risk-based focus is preferred.
C . Incorrect:
Frequent audits may still be required depending on organizational needs.
Relevant Standard Reference:
A . Correct Answer:
Combining multiple audit test plans ensures different perspectives and validation techniques are applied, improving audit accuracy.
ISO 19011:2018 encourages a diversified approach to auditing to ensure comprehensive results.
B . Incorrect:
Not all areas require equal auditing-risk-based focus is preferred.
C . Incorrect:
Frequent audits may still be required depending on organizational needs.
Relevant Standard Reference:
Question 135
您是一位經驗豐富的 ISMS 審核團隊負責人,正在與分配給您的審核團隊的正在接受培訓的審核員進行交談。您希望確保他們了解計劃-實施-檢查-行動週期的檢查階段對於資訊安全管理系統的運作的重要性。
您可以透過要求他選擇最能完成句子的單字來做到這一點:
要使用最佳單字完成句子,請按一下要完成的空白部分,使其以紅色突出顯示,然後從下面的選項中按一下適用的文字。或者,您可以將該選項拖曳到適當的空白部分。
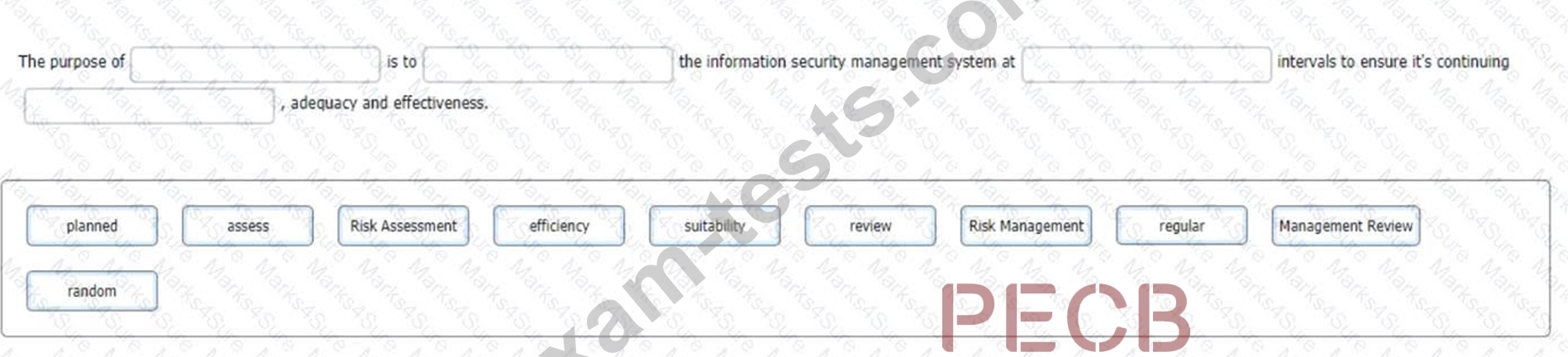
您可以透過要求他選擇最能完成句子的單字來做到這一點:
要使用最佳單字完成句子,請按一下要完成的空白部分,使其以紅色突出顯示,然後從下面的選項中按一下適用的文字。或者,您可以將該選項拖曳到適當的空白部分。

Correct Answer:
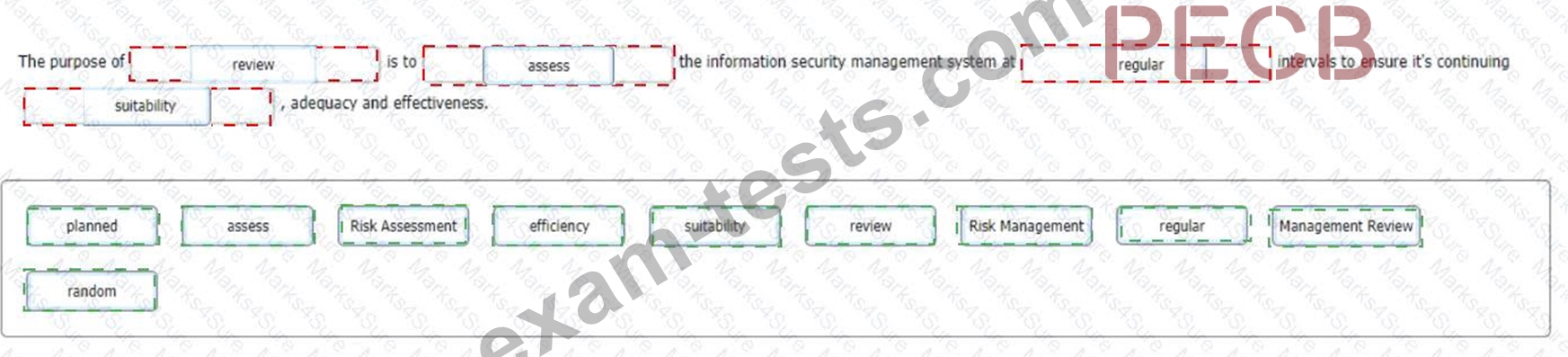
Explanation:
* Review is the third stage of the Plan-Do-Check-Act (PDCA) cycle, which is a four-step model for implementing and improving an information security management system (ISMS) according to ISO
/IEC 27001:202212. Review involves assessing and measuring the performance of the ISMS against the established policies, objectives, and criteria12.
* Assess is the verb that describes the action of reviewing the ISMS. Assess means to evaluate, analyze, or measure something in a systematic and objective manner3. Assessing the ISMS involves collecting and verifying audit evidence, identifying strengths and weaknesses, and determining the degree of conformity or nonconformity12.
* Regular is the adjective that describes the frequency or interval of reviewing the ISMS. Regular means occurring or done at fixed or uniform intervals4. Reviewing the ISMS at regular intervals means conducting internal audits and management reviews periodically, such as annually, quarterly, or monthly, depending on the needs and risks of the organization12.
* Suitability is one of the attributes that describes the quality or outcome of reviewing the ISMS. Suitability means being appropriate or fitting for a particular purpose, person, or situation5. Reviewing the ISMS for suitability means ensuring that it is aligned with the organization's strategic direction, business objectives, and information security requirements12.
References :=
* ISO/IEC 27001:2022 Information technology - Security techniques - Information security management systems - Requirements
* ISO/IEC 27003:2022 Information technology - Security techniques - Information security management systems - Guidance
* Assess | Definition of Assess by Merriam-Webster
* Regular | Definition of Regular by Merriam-Webster
* Suitability | Definition of Suitability by Merriam-Webster
- Latest Upload
- 154Fortinet.FCP_FAZ_AD-7.4.v2026-01-16.q115
- 141PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166
- 126Talend.Talend-Core-Developer.v2026-01-15.q20
- 170Salesforce.Marketing-Cloud-Administrator.v2026-01-15.q146
- 244Salesforce.ADX-211.v2026-01-14.q223
- 136Salesforce.B2B-Solution-Architect.v2026-01-14.q111
- 143BICSI.RCDD.v2026-01-14.q121
- 125NBMTM.BCMTMS.v2026-01-14.q33
- 128Microsoft.GH-200.v2026-01-13.q64
- 147SAP.C_C4HCX_2405.v2026-01-13.q80
[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166 Practice Test

