Question 56
Your network contains an Active Directory domain named contoso.com. The domain contains a VPN server named VPN1 that runs Windows Server 2016 and has the Remote Access server role installed.
You have a Microsoft Azure subscription.
You are deploying Azure Advanced Threat Protection (ATP)
You install an Azure ATP standalone sensor on a server named Server1 that runs Windows Server 2016.
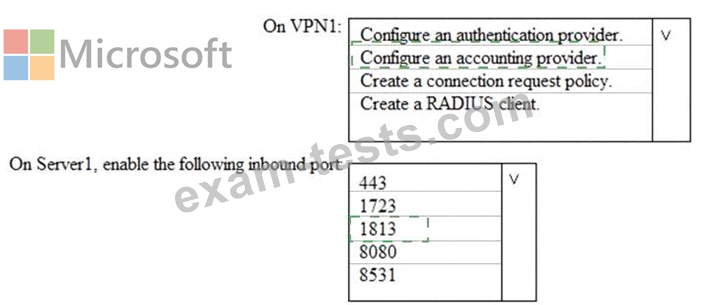
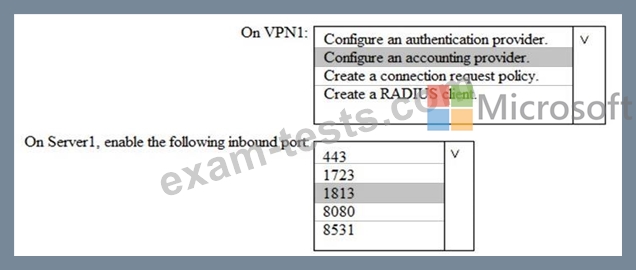
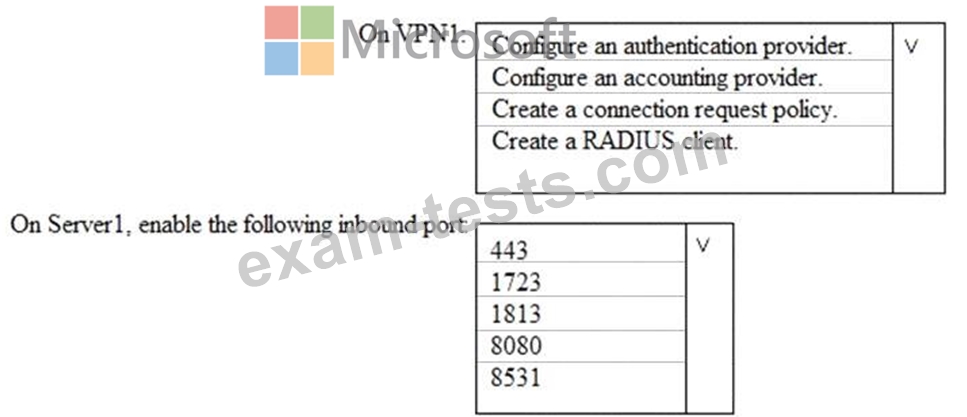
You need to integrate the VPN and Azure ATP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft Azure subscription.
You are deploying Azure Advanced Threat Protection (ATP)
You install an Azure ATP standalone sensor on a server named Server1 that runs Windows Server 2016.
You need to integrate the VPN and Azure ATP.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 57
You have a Microsoft 365 tenant.
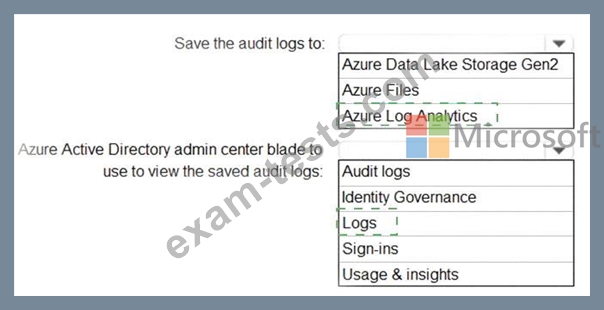
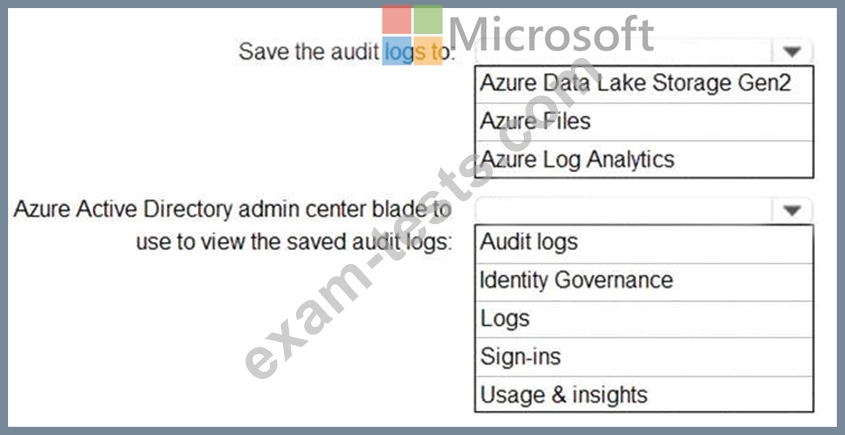
You need to retain Azure Active Directory (Azure AD) audit logs for two years. Administrators must be able to query the audit log information by using the Azure Active Directory admin center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to retain Azure Active Directory (Azure AD) audit logs for two years. Administrators must be able to query the audit log information by using the Azure Active Directory admin center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 58
You have a Microsoft 365 E5 subscription.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
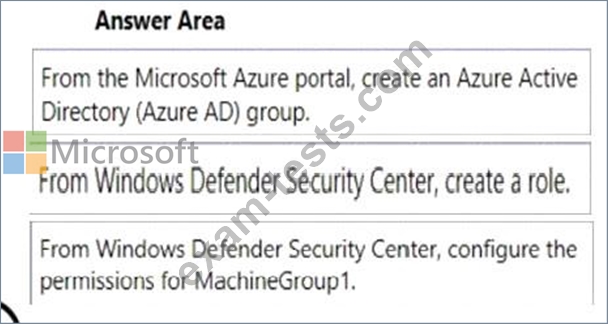
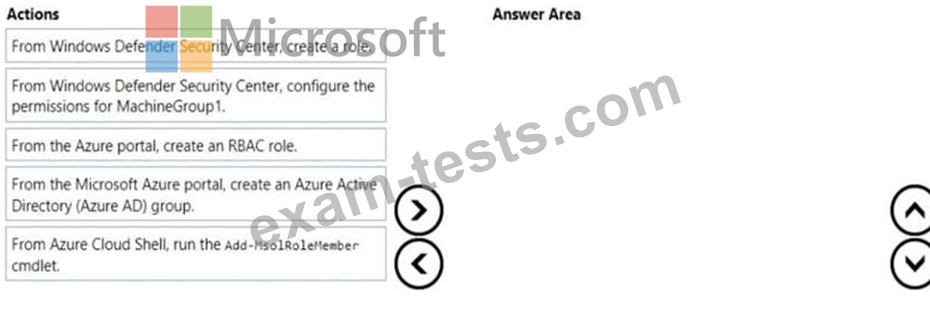
You create a Windows Defender machine group named MachineGroupl.
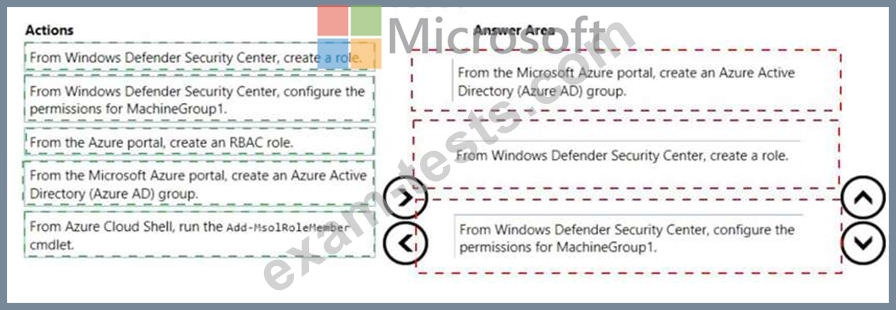
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
All computers run Windows 10 and are onboarded to Windows Defender Advanced Threat Protection (Windows Defender ATP).
You create a Windows Defender machine group named MachineGroupl.
You need to enable delegation for the security settings of the computers in MachineGroupl.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 59
You have a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. All the devices in the tenant are managed by using Microsoft Intune.
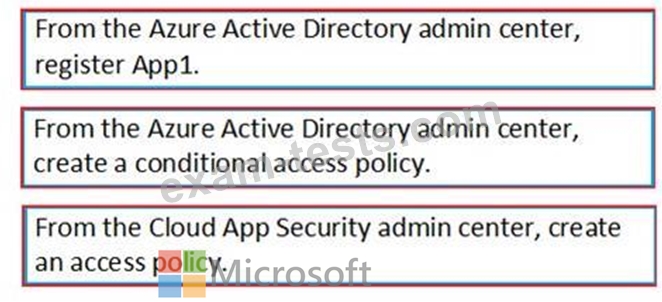
You purchase a cloud app named App1 that supports session controls.
You need to ensure that access to App can be reviewed in real time.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You purchase a cloud app named App1 that supports session controls.
You need to ensure that access to App can be reviewed in real time.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 60
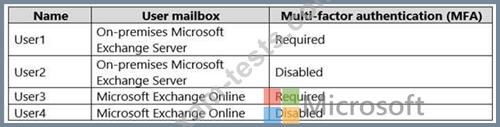
You have a hybrid deployment of Microsoft 365 that contains the users shown in the following table.
You plan to use Microsoft 365 Attack Simulator.
You need to identify the users against which you can use Attack Simulator.
Which users should you identify?

You plan to use Microsoft 365 Attack Simulator.
You need to identify the users against which you can use Attack Simulator.
Which users should you identify?