Question 66
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.
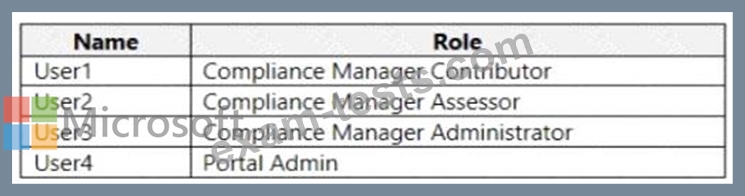
You discover that all the users in the subscription can access Compliance Manager reports.
The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend assigning the Compliance Manager Reader role to User1.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription that contains the users shown in the following table.

You discover that all the users in the subscription can access Compliance Manager reports.
The Compliance Manager Reader role is not assigned to any users.
You need to recommend a solution to prevent a user named User5 from accessing the Compliance Manager reports.
Solution: You recommend assigning the Compliance Manager Reader role to User1.
Does this meet the goal?
Question 67
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-Mailbox -Identity "User1" -AuditEnabled $truecommand.
Does that meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-Mailbox -Identity "User1" -AuditEnabled $truecommand.
Does that meet the goal?
Question 68
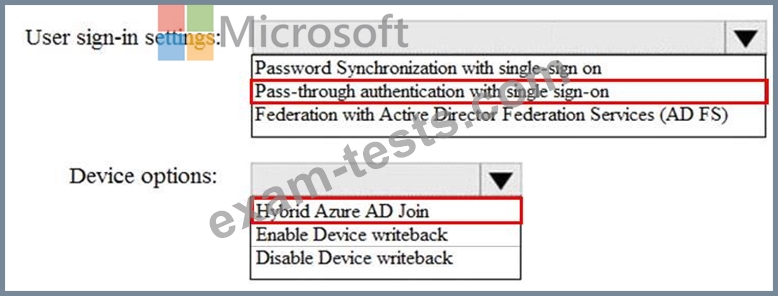
How should you configure Azure AD Connect? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
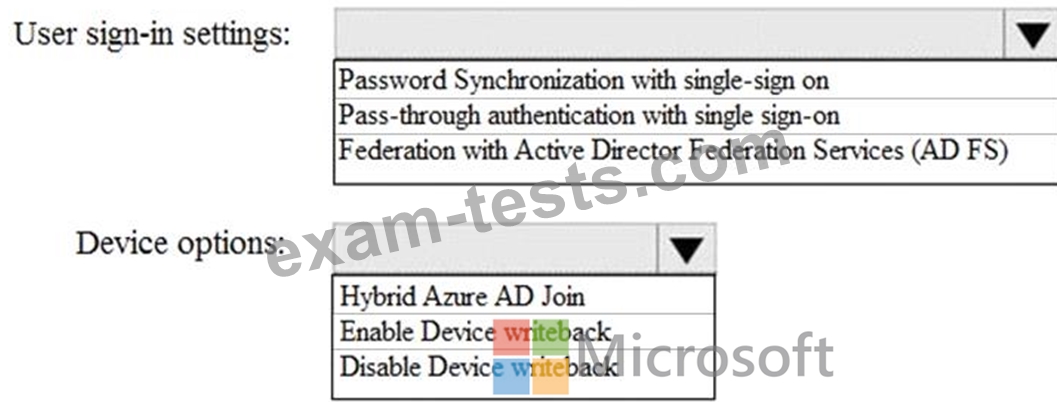
NOTE: Each correct selection is worth one point.

Question 69
Note: This question is part of series of questions that present the same scenario. Each question in
the series contains a unique solution that might meet the stated goals. Some question sets might
have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure
AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the
tenant. Azure AD Connect has the following settings:
Source Anchor: objectGUID

Password Hash Synchronization: Disabled

Password writeback: Disabled

Directory extension attribute sync: Disabled

Azure AD app and attribute filtering: Disabled

Exchange hybrid deployment: Disabled

User writeback: Disabled

You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Azure AD app and attribute filtering settings.
Does that meet the goal?
the series contains a unique solution that might meet the stated goals. Some question sets might
have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these
questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that is associated to a Microsoft Azure Active Directory (Azure
AD) tenant named contoso.com.
You use Active Directory Federation Services (AD FS) to federate on-premises Active Directory and the
tenant. Azure AD Connect has the following settings:
Source Anchor: objectGUID

Password Hash Synchronization: Disabled

Password writeback: Disabled

Directory extension attribute sync: Disabled

Azure AD app and attribute filtering: Disabled

Exchange hybrid deployment: Disabled

User writeback: Disabled

You need to ensure that you can use leaked credentials detection in Azure AD Identity Protection.
Solution: You modify the Azure AD app and attribute filtering settings.
Does that meet the goal?
Question 70
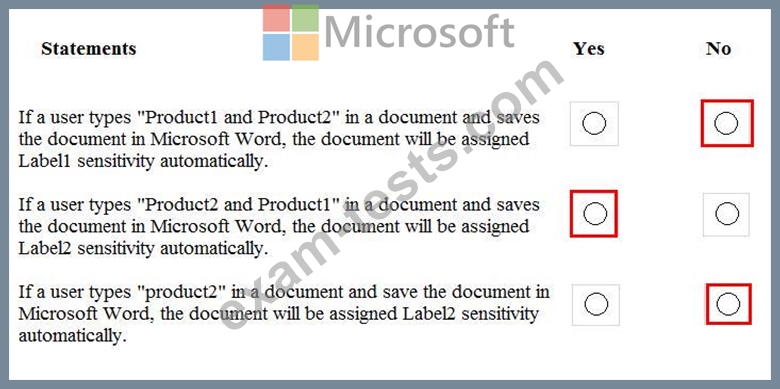
You have the Microsoft conditions shown in the following table.
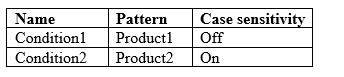
You have the Azure Information Protection labels shown in the following table.
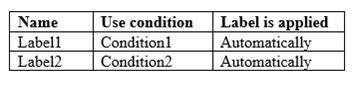
You have the Azure Information Protection policies shown in the following table.
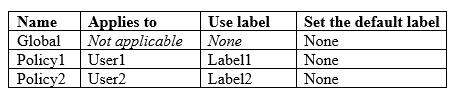
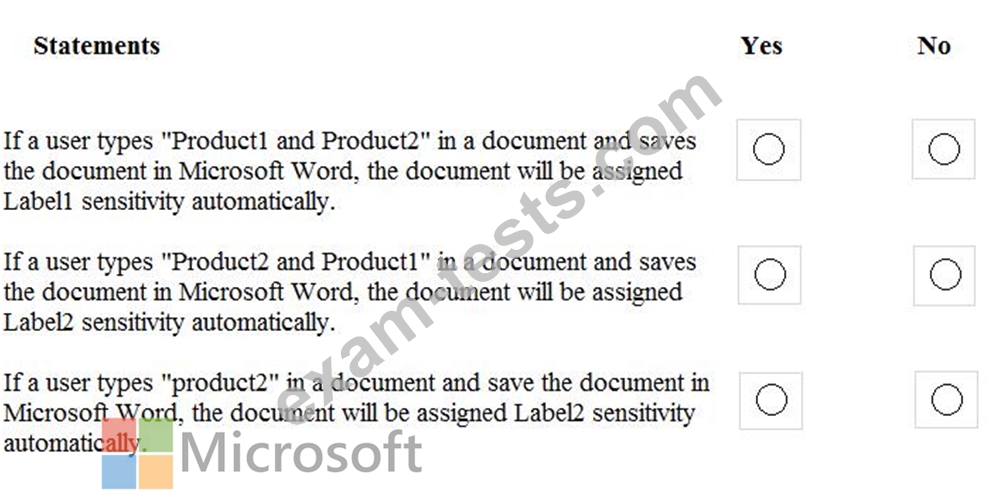
For each of the following statements, select Yes if the statement is true. Otherwise, select No.

You have the Azure Information Protection labels shown in the following table.

You have the Azure Information Protection policies shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.