Question 251
A network administrator is going to be performing a major upgrade to the network. Which of the following should the administrator use in case of a failure?
Question 252
A technician discovers that a malware infection has damaged part of the Windows TCP/IP stack.
Which of the following commands can help repair the damage?
Which of the following commands can help repair the damage?
Question 253
While working on a Linux-based OS, a technician experiences an issue accessing some servers and some sites by name. Which of the following command-line tools should the technician use to assist in troubleshooting?
Question 254
Joe, a user, is having issues when trying to access certain web pages. Upon navigating to a web page, it seems like it connects, but then presents the following message:

Joe has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker's desktop, but it still presented with this error.
Which of the following is the MOST likely cause of this error?

Joe has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker's desktop, but it still presented with this error.
Which of the following is the MOST likely cause of this error?
Question 255
Drag and Drop Question
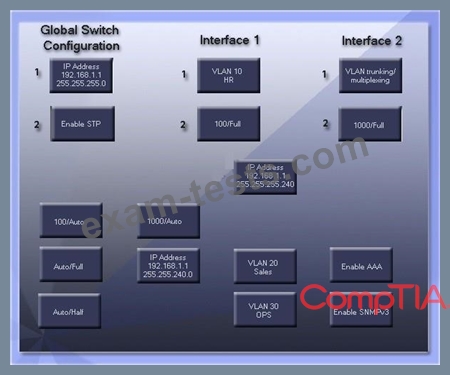
GigSwitch1 is currently configured with a speed of 100 and Duplex is set to Auto on all interfaces.
Interface 2 will be connected to GigSwitch2 which is used for all departments. Interface 1 will be used for HR traffic only.
GigSwitch1 needs to be configured with the following parameters:
* Configure the necessary protocol to prevent switching loops
* Configure GigSwitch1 with a /24 IP address for management
* Traffic across Interface 1 needs to be forced to accept and receive
up to 100Mbps data at the same time
* Traffic across Interface 2 needs to be forced to use Gigabit speeds
and maximum performance
Drag and drop the appropriate configurations to their corresponding requirements.
All placeholders must be filled. Not all configurations will be used.
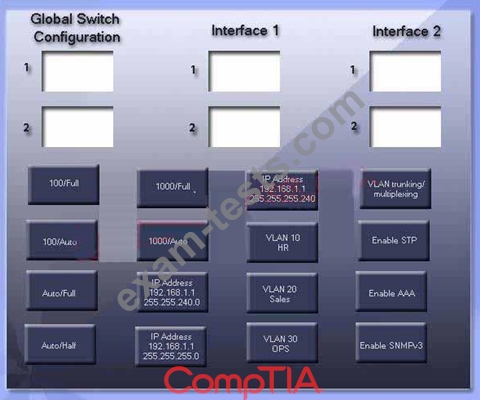
GigSwitch1 is currently configured with a speed of 100 and Duplex is set to Auto on all interfaces.
Interface 2 will be connected to GigSwitch2 which is used for all departments. Interface 1 will be used for HR traffic only.
GigSwitch1 needs to be configured with the following parameters:
* Configure the necessary protocol to prevent switching loops
* Configure GigSwitch1 with a /24 IP address for management
* Traffic across Interface 1 needs to be forced to accept and receive
up to 100Mbps data at the same time
* Traffic across Interface 2 needs to be forced to use Gigabit speeds
and maximum performance
Drag and drop the appropriate configurations to their corresponding requirements.
All placeholders must be filled. Not all configurations will be used.