Question 256
A company's Chief Information Security Officer (CISO) has decided to increase overall network security by implementing two-factor authentication. All users already have username/password combinations and require an additional factor of authentication. Which of the following would satisfy the requirements?
Question 257
Several network changes were made to a company's firewall, and users have no longer been able to access websites by name. A technician suspects there is a port misconfiguration. Which of the following ports was misconfigured?
Question 258
An assistant systems analyst reports the following findings of an investigation of slow Internet connections in a remote office to the senior systems analyst:
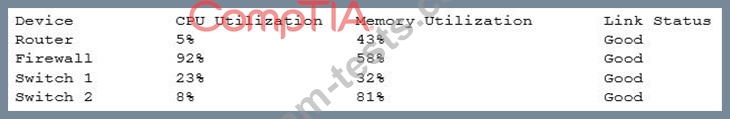
Which of the following devices is causing the issue?

Which of the following devices is causing the issue?
Question 259
Joe, a network technician, wants to locally back up several router and switch configurations. He wants to store them on a server that can be accessed easily for recovery without authentication. Which of the following servers should Joe use?
Question 260
A company has hundreds of nodes on a single subnet and has decided to implement VLANs. Which of the
following BEST describes the benefit of this approach?
following BEST describes the benefit of this approach?

