Question 61
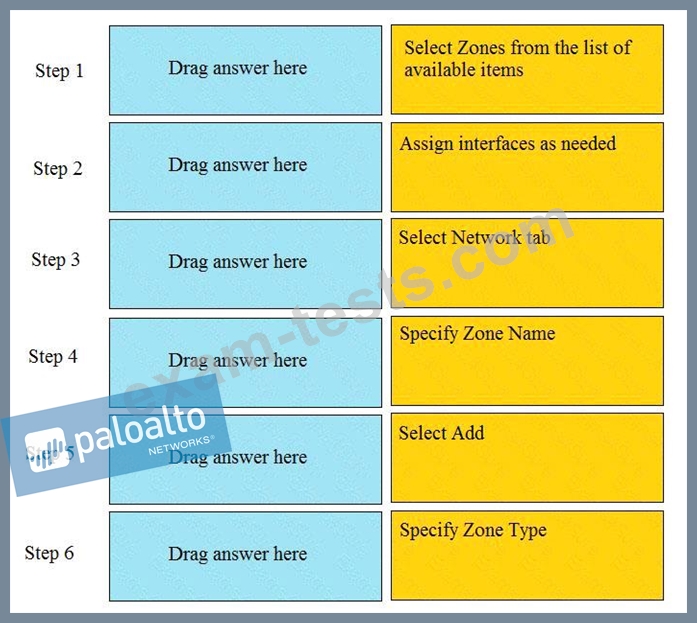
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.

Question 62
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
Question 63
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
Which Security policy action should the administrator select?
Question 64
Which two features can be used to tag a user name so that it is included in a dynamic user group? (Choose two)
Question 65
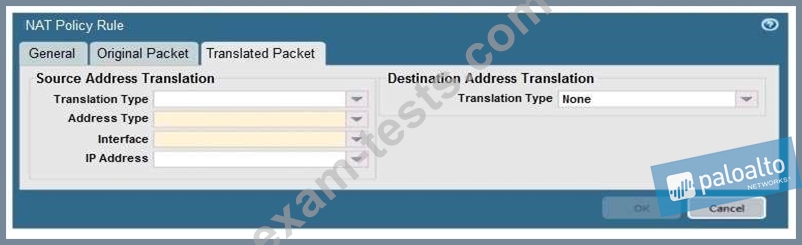
When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None?