Question 46
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
Question 47
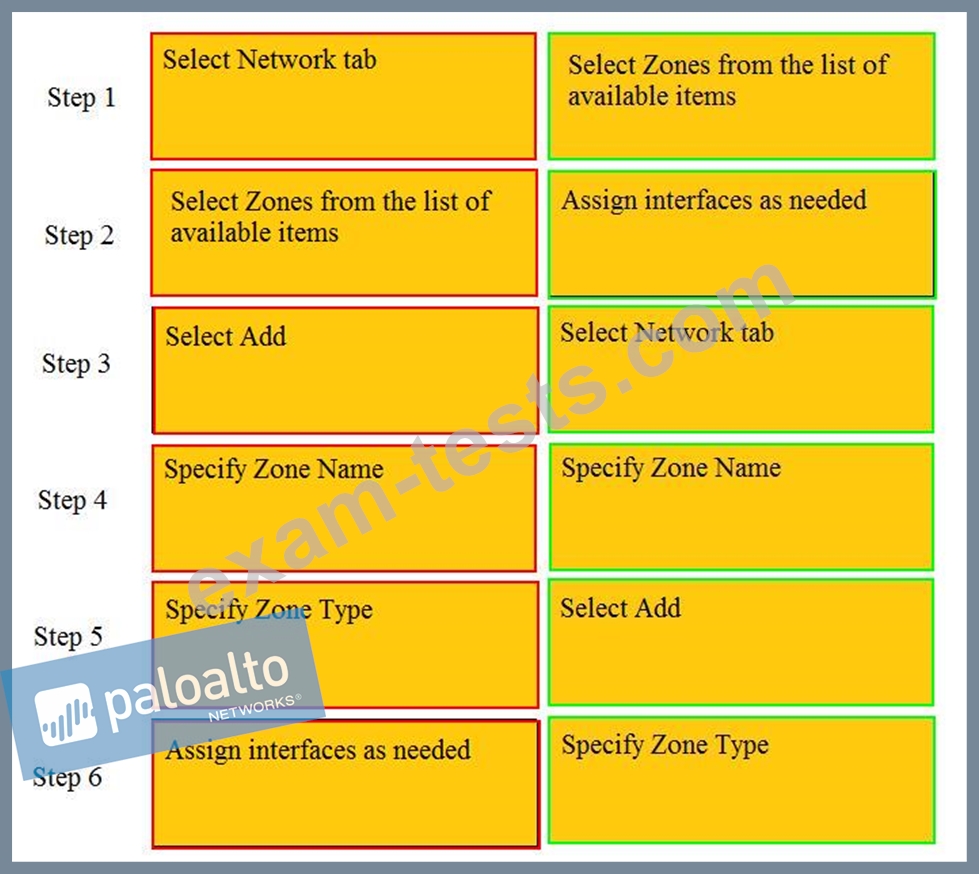
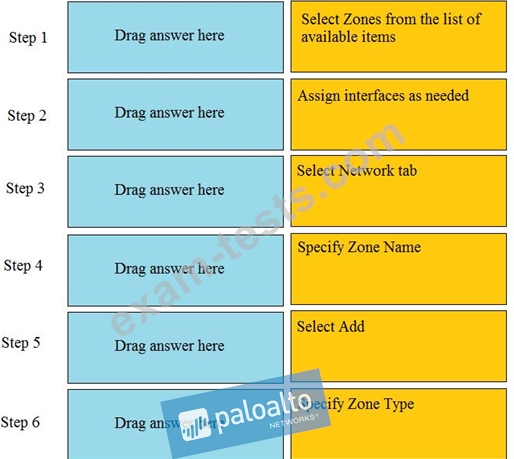
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.

Question 48
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall's signature database has been updated?
(Choose two.)
(Choose two.)
Question 49
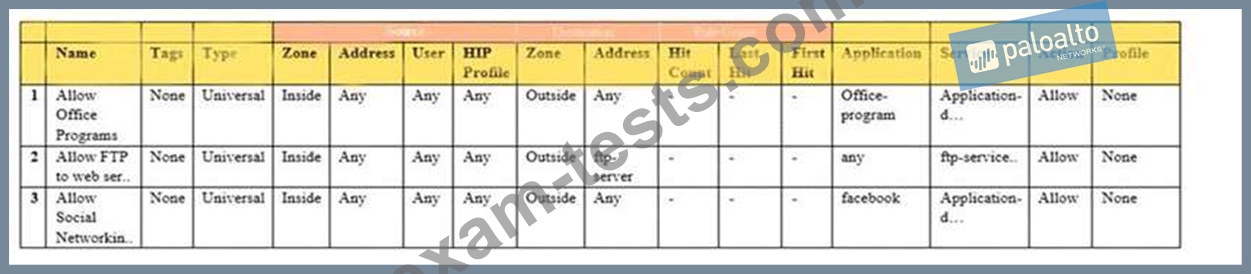
Given the image, which two options are true about the Security policy rules. (Choose two.)

Question 50
Which URL profiling action does not generate a log entry when a user attempts to access that URL?